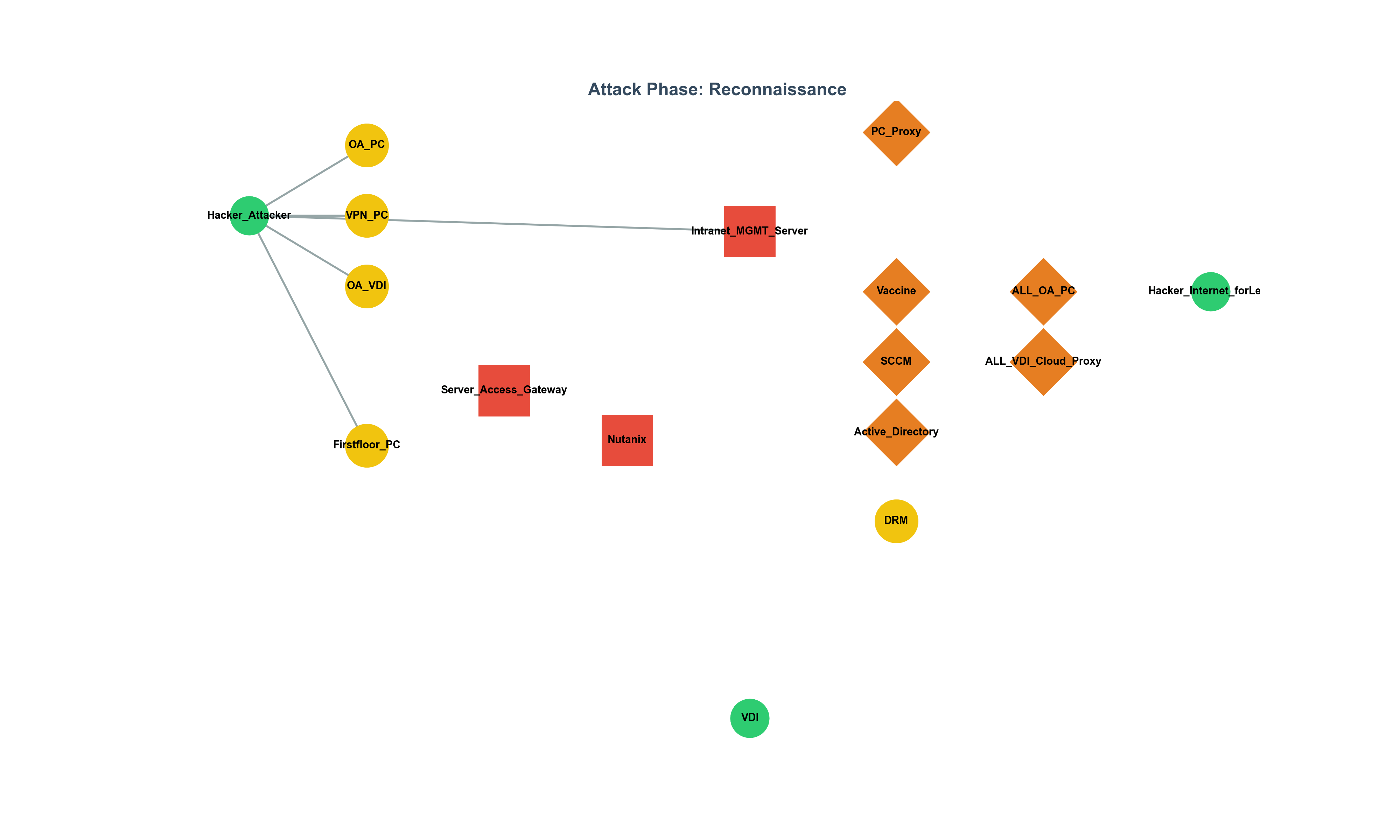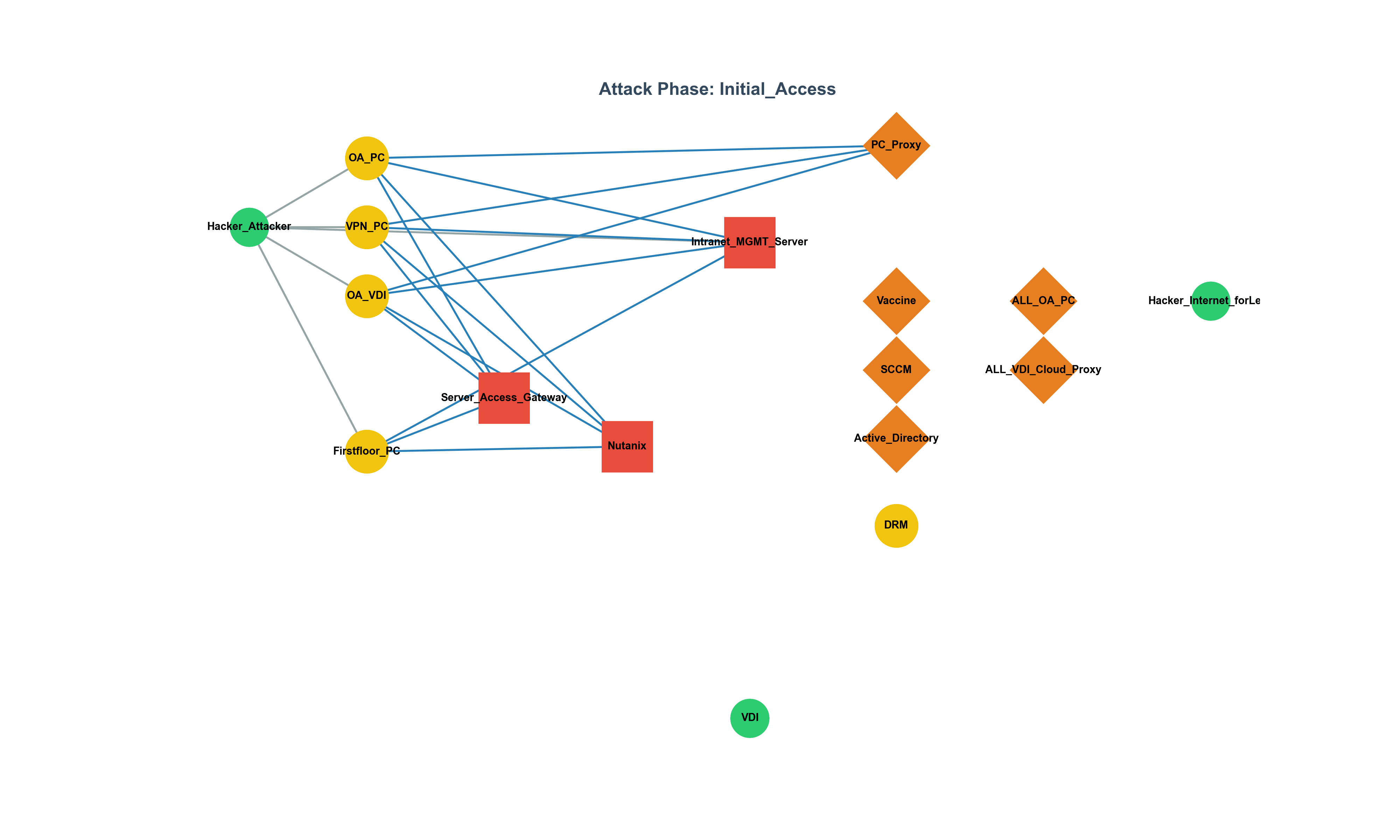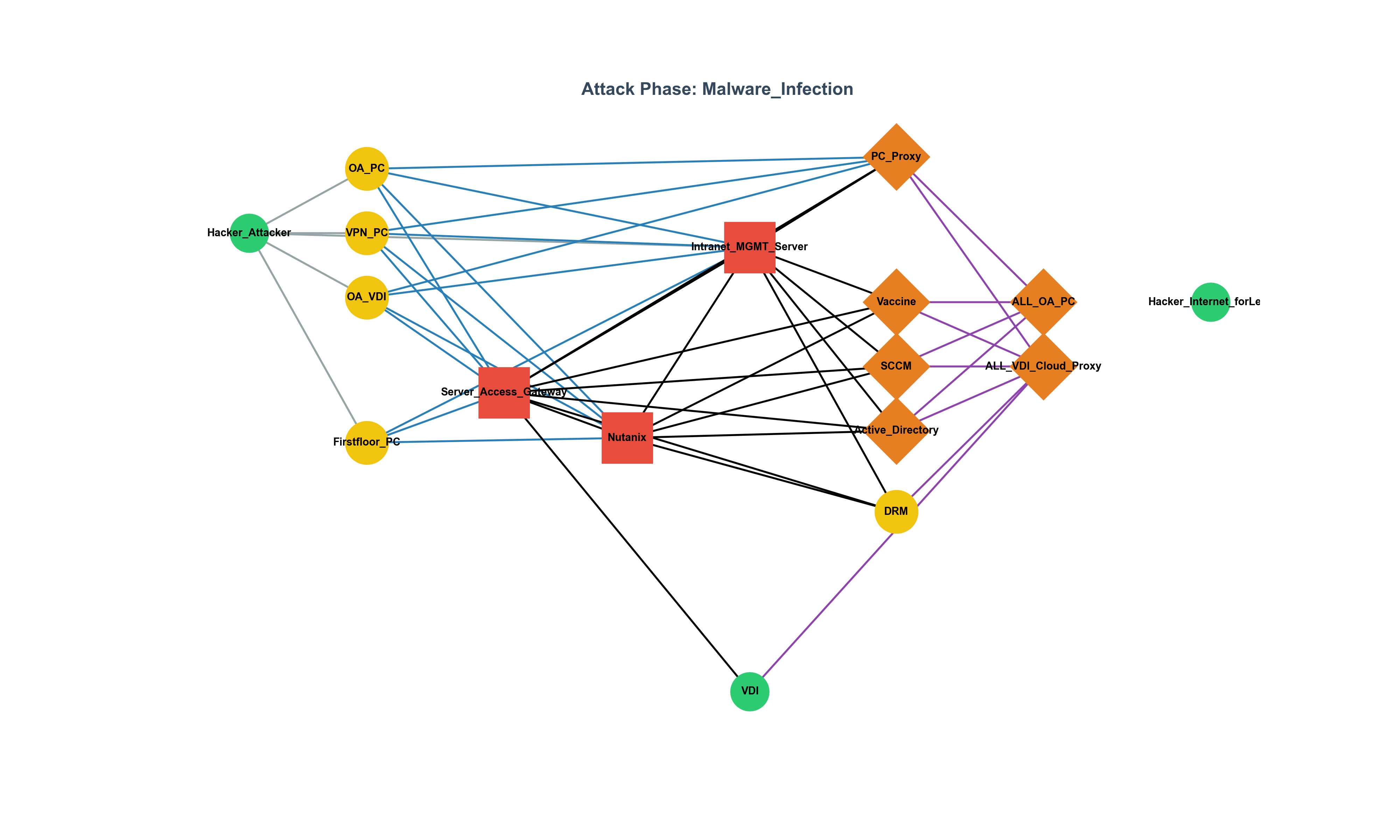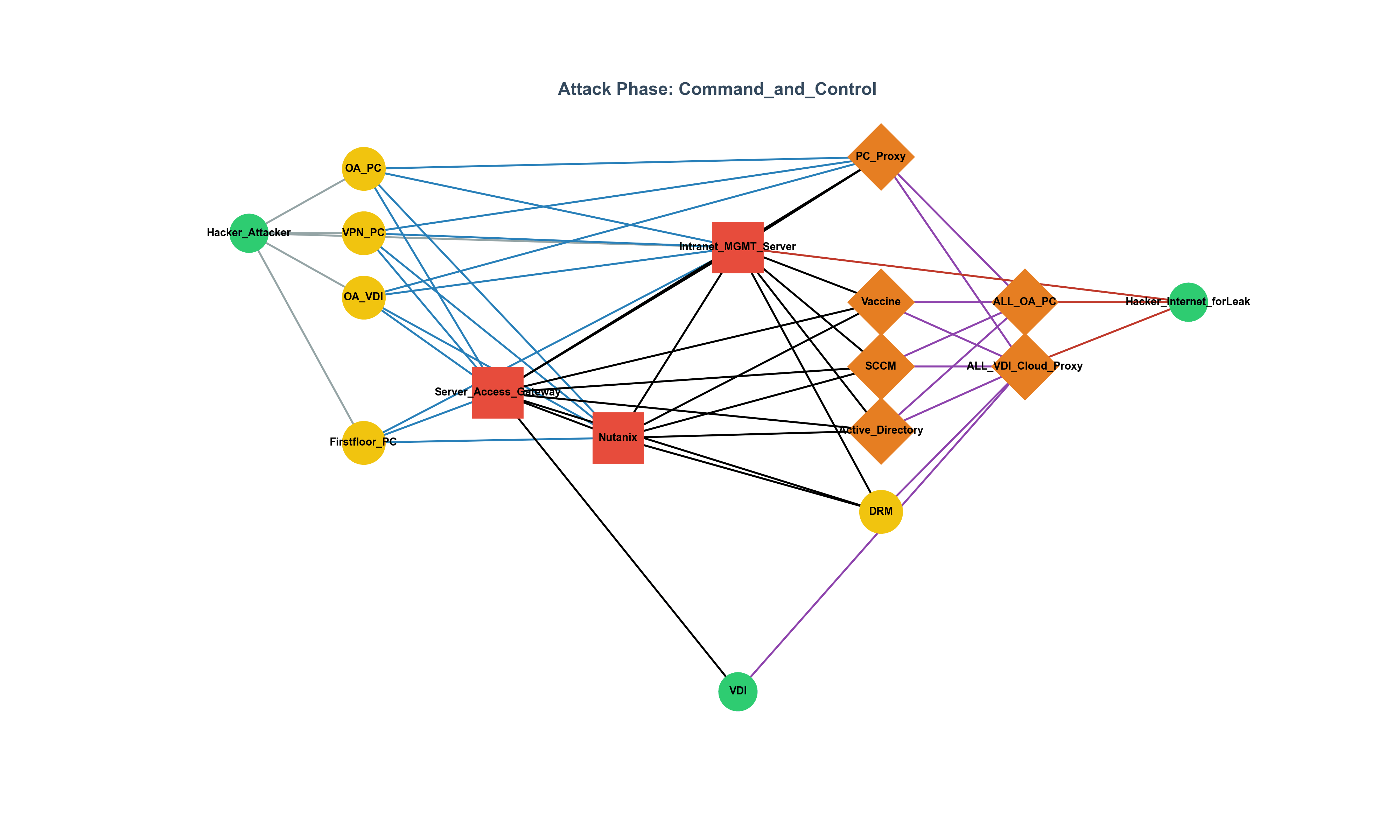
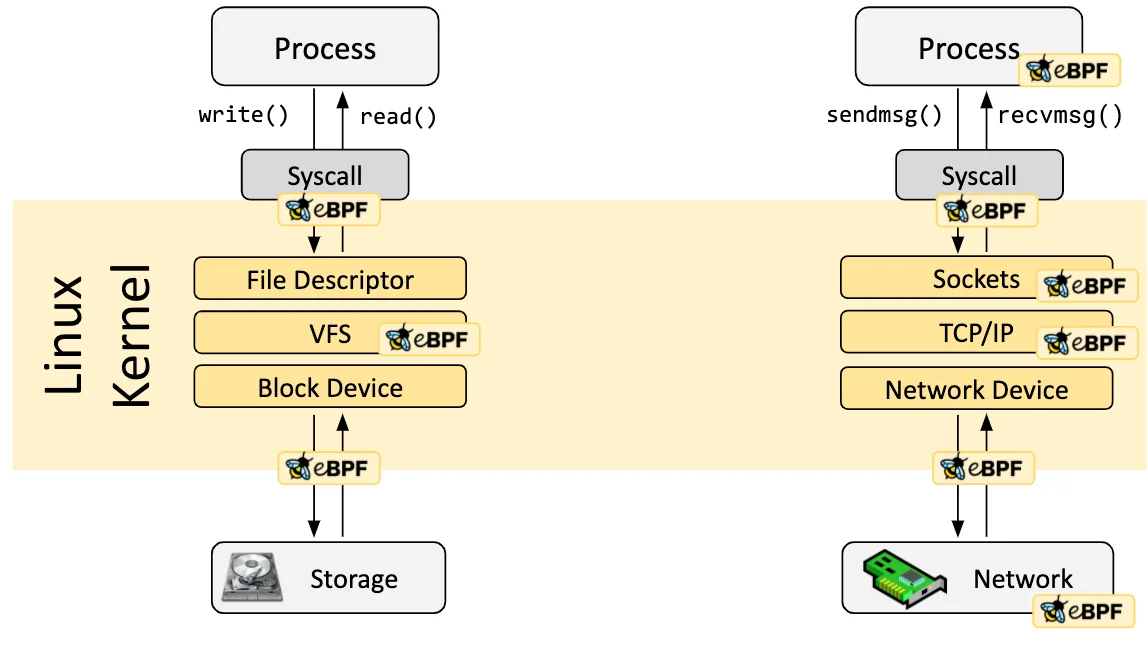
The Limitations of 'Secure' SSRF Patches: Advanced Bypasses and Defense-in-Depth
No Silver Bullet: Folklore & Modern Meaning The phrase “no silver bullet” originated in European folklore, where silver bullets were believed to be uniquely effective against supernatural creatures like werewolves or vampires. The earliest documented use appears in Walter Scott’s 1816 Tales of My Landlord, and historical cases such as the 1765 Beast of Gévaudan reference silver bullets as a last resort against mysterious threats. Over time, the expression evolved: today, “no silver bullet” means there is no single, simple solution to complex problems—a message popularized in software engineering by Fred Brooks’ 1986 essay. This post applies that lesson to SSRF defense: beware of one-size-fits-all fixes, and look deeper than folklore or quick patches. ...