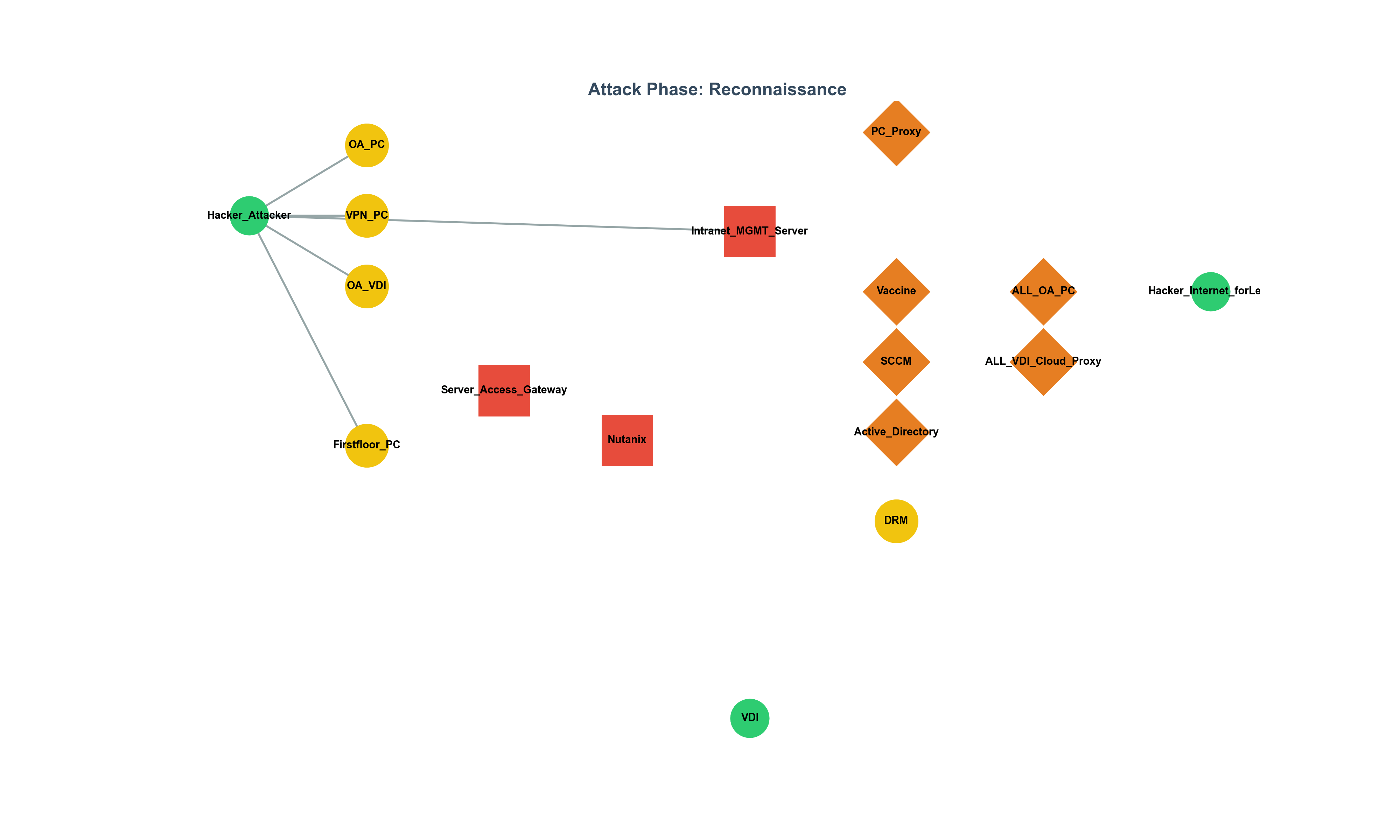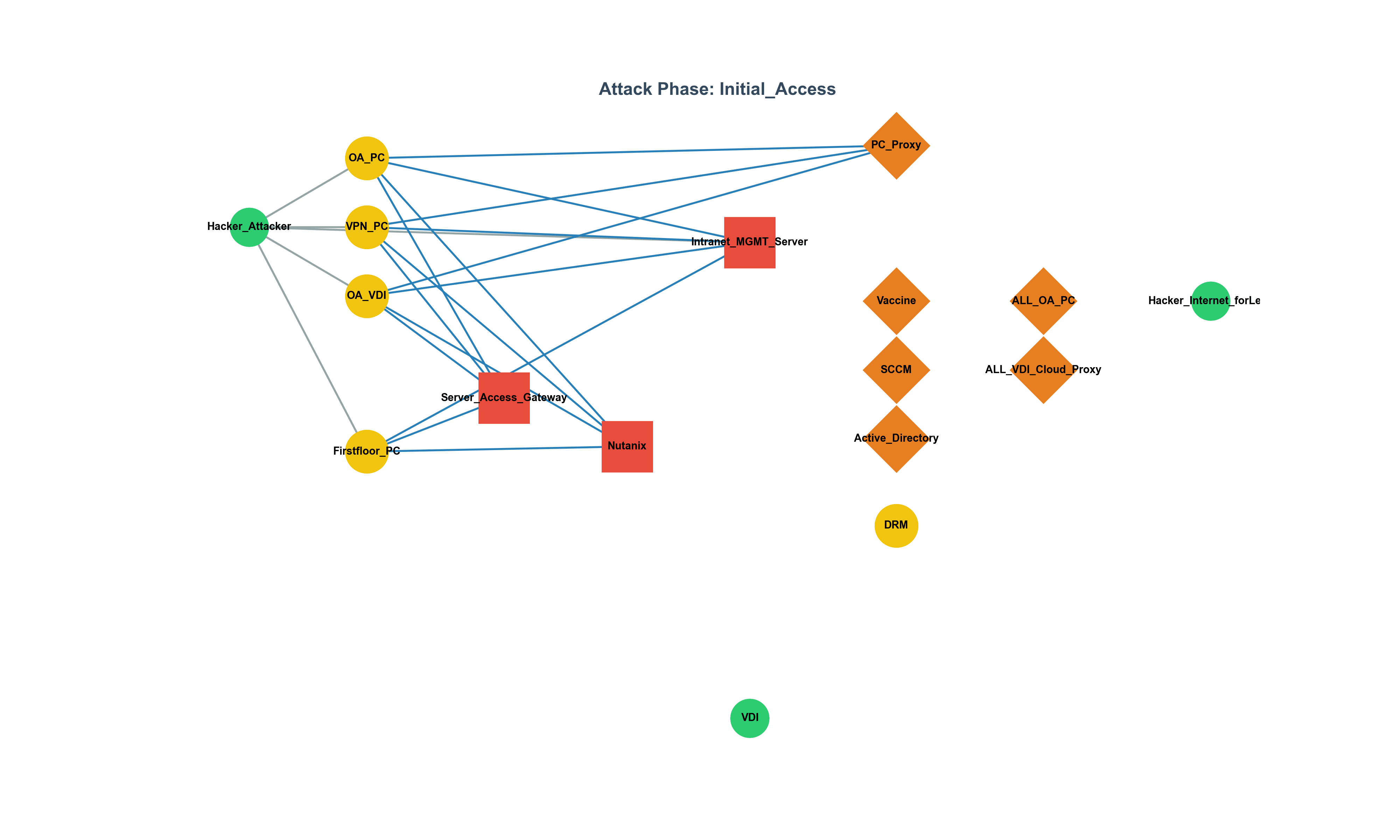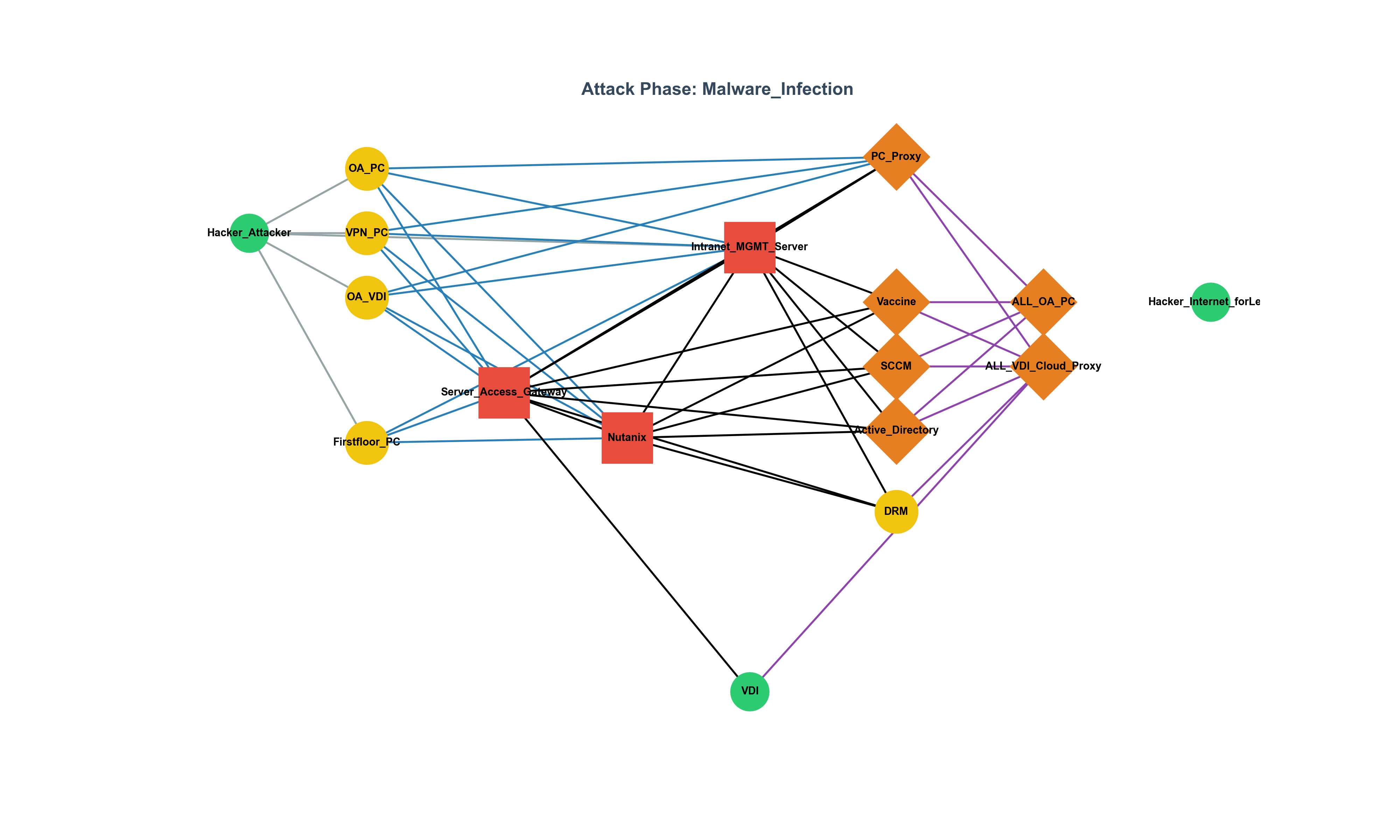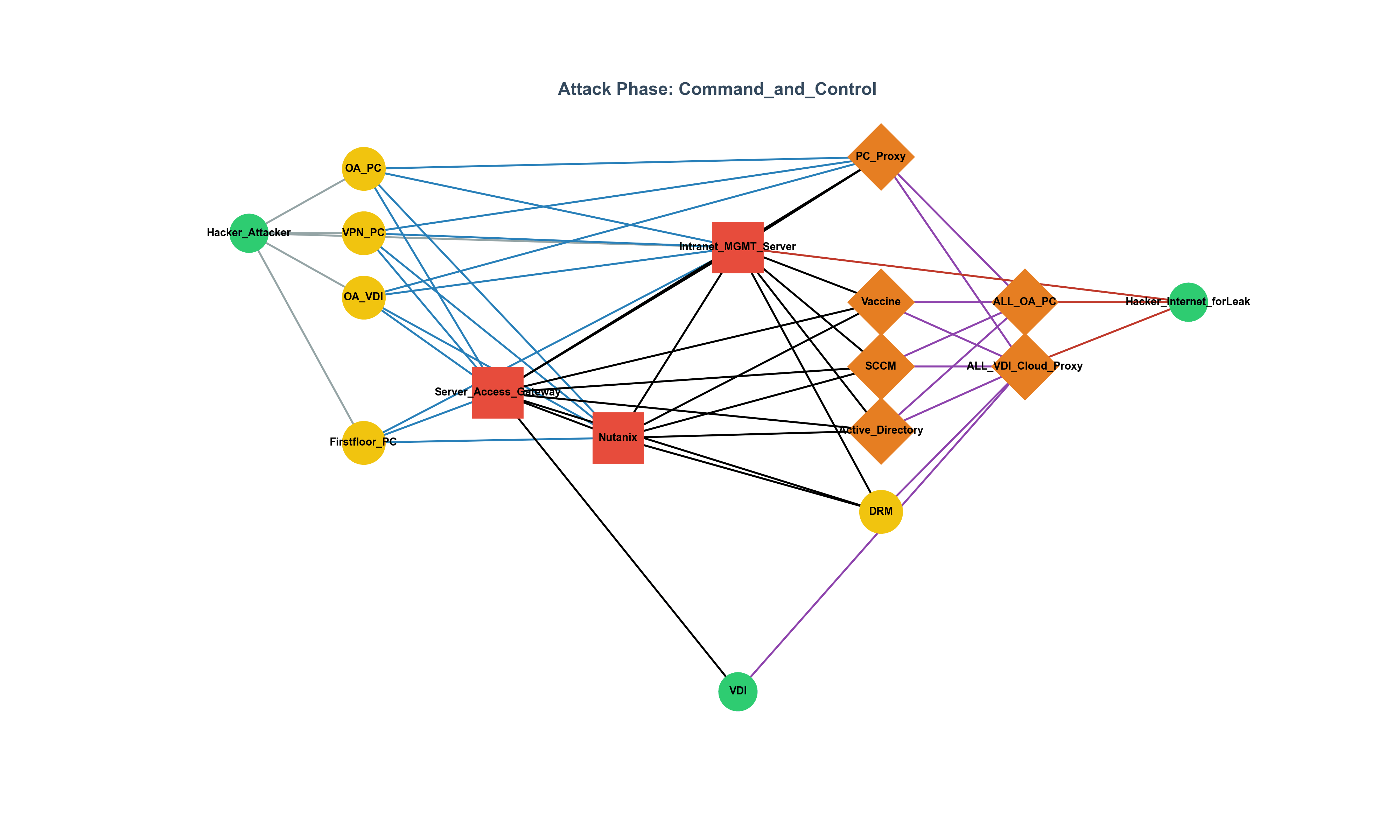
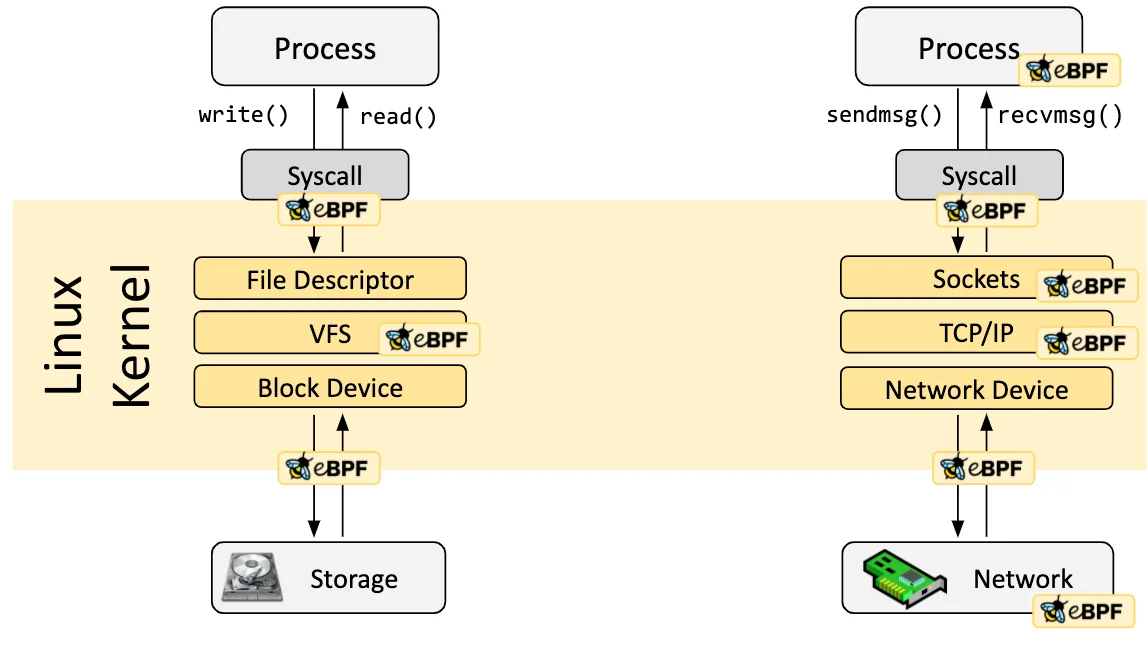
The Gap Between CISO Strategy and Execution: The WAF Debate and Field Leadership Report
Preface: The Crack Between Philosophy and Execution First half of 202x. When the group’s penetration test report stated, “SQL Injection possible in WAF-unprotected section,” the CISO was silent for a while. The report was blunt, the attack was classic, and there was no defense. “Was I wrong? Or did they misunderstand my intention…?” The CISO was a leader of strong conviction. He believed that with a strategy of “IPS + security by design,” it was possible to build a system robust enough to forgo WAF deployment. In fact, for years, this strategy contributed to the organization’s threat detection and incident prevention. ...