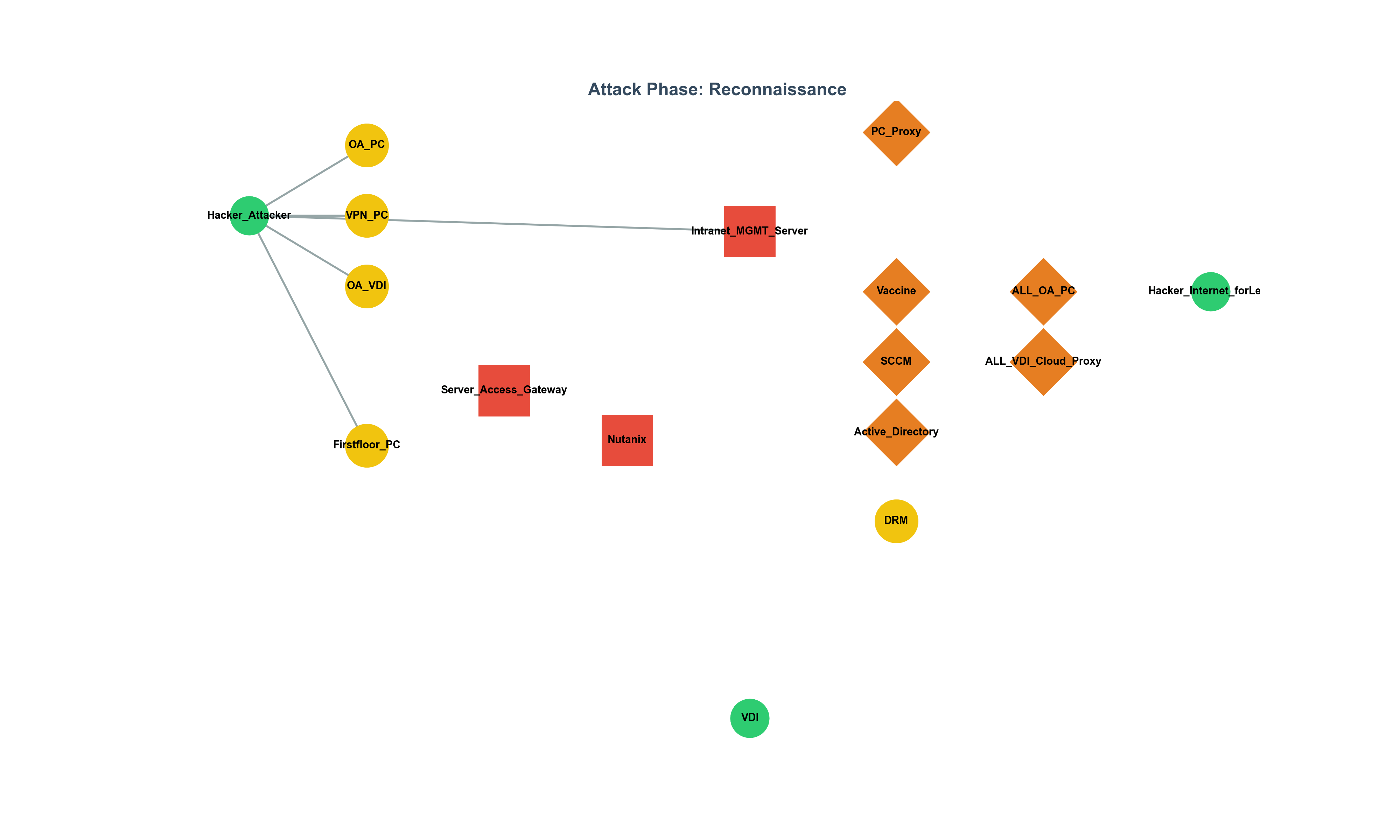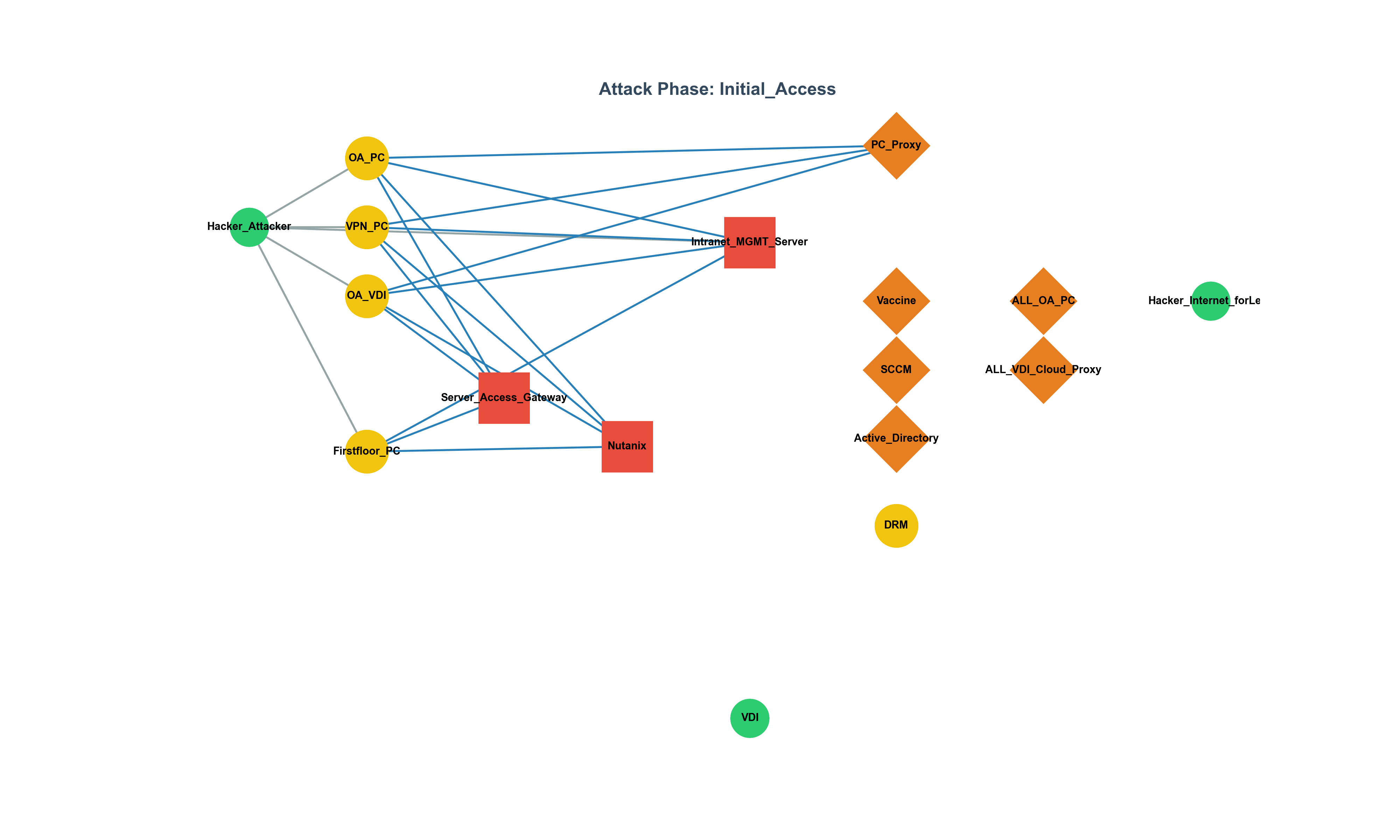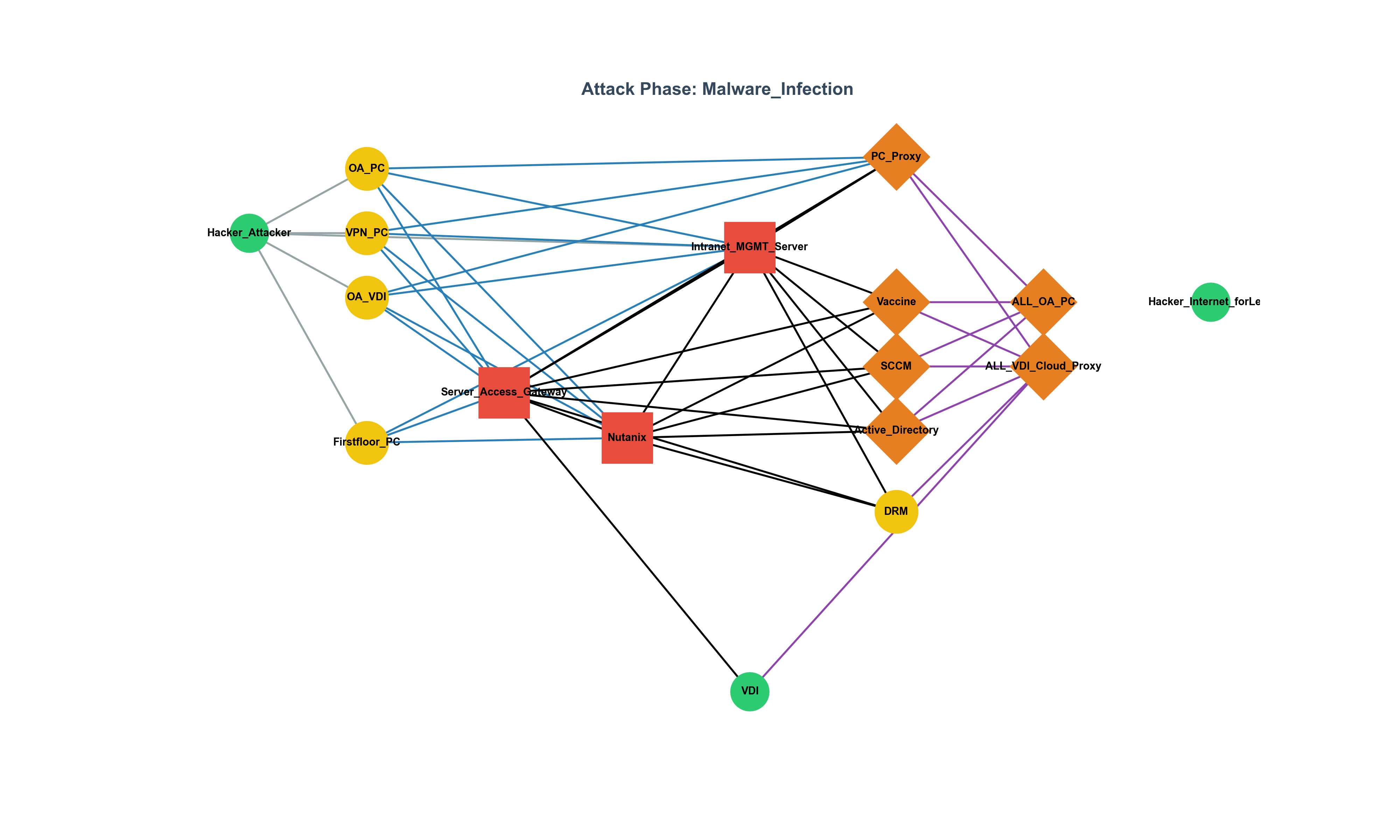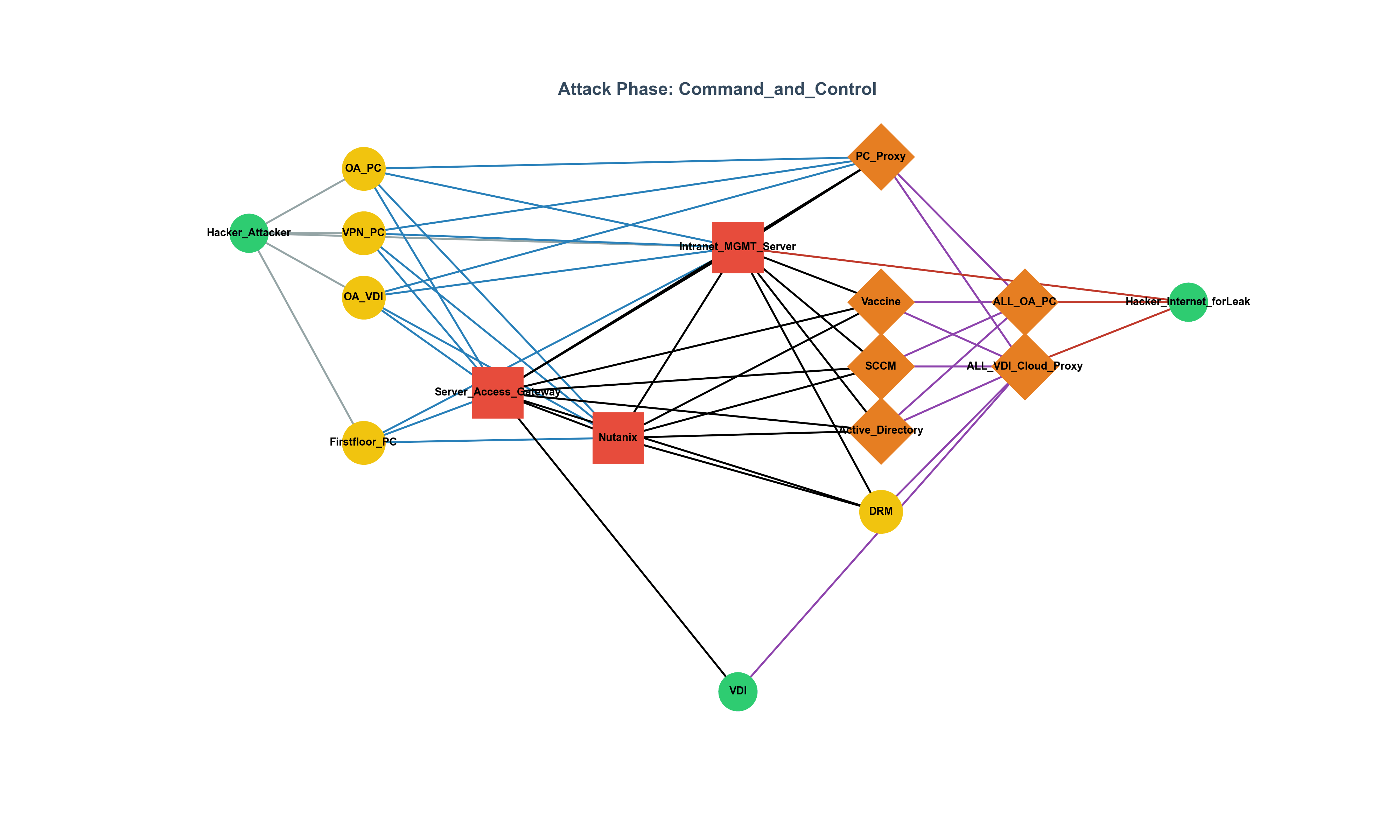
XML-RPC Security Series:
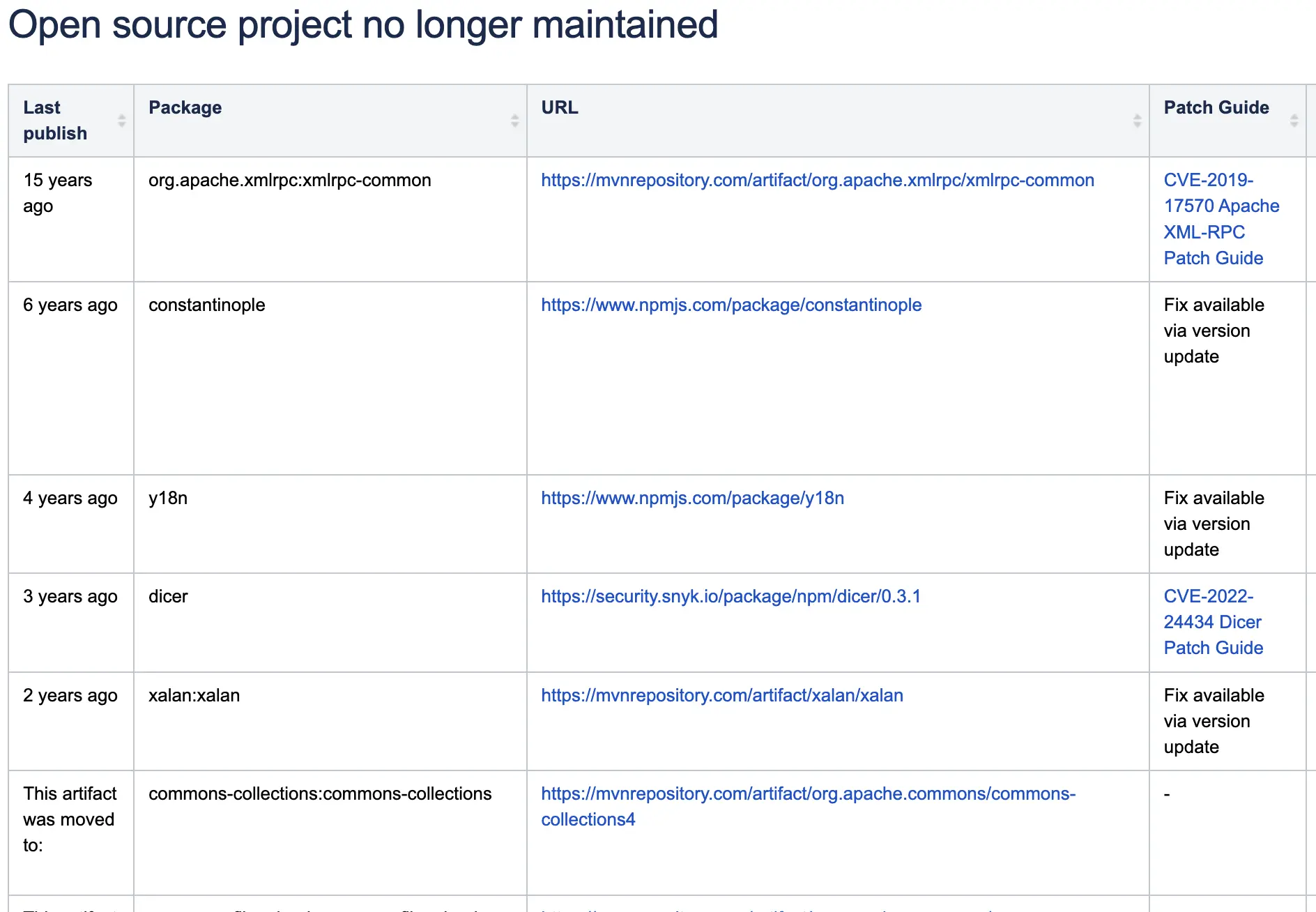
Series 1 - XML-RPC Security Vulnerabilities Analysis and Mitigation Strategies Series 2 - CVE-2019-17570: Apache XML-RPC Exploit Series 3 - Exception Serialization Patterns in OpenStack Nova: Theoretical RCE Risks and Lessons Learned Summary Overview of XML-RPC Vulnerabilities: As a lightweight remote call protocol for inter-system communication, XML-RPC is exposed to various threats such as RCE, XXE, DDoS, and privilege escalation. Notable Cases: NodeBB (CVE-2023-43187), Apache OFBiz (CVE-2020-9496), PHP XML-RPC (CVE-2005-1921), etc. Real-World Use Cases: In addition to WordPress, Bugzilla, ManageEngine, and Apache OFBiz, XML-RPC is still used in some legacy systems. Mitigation Strategies: Disabling XML-RPC, enhancing input validation, reinforcing authentication systems, applying up-to-date security patches, implementing access control, and deploying WAFs. What is XML-RPC? XML-RPC (XML Remote Procedure Call) is a remote procedure call protocol that uses XML as its data format and HTTP as its transport mechanism. Proposed jointly by Dave Winer and Microsoft in 1998, it was designed to simplify cross-platform communication.
...