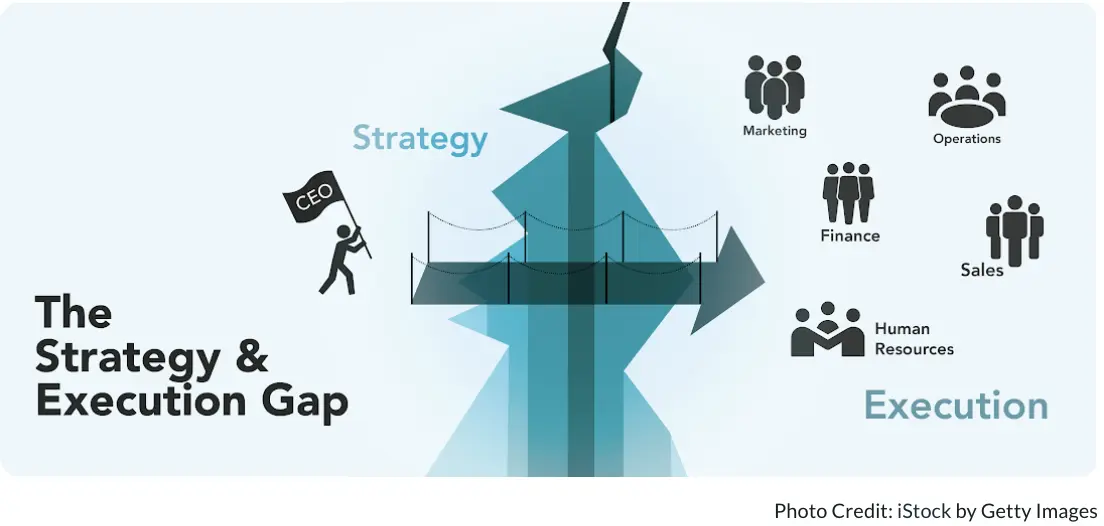
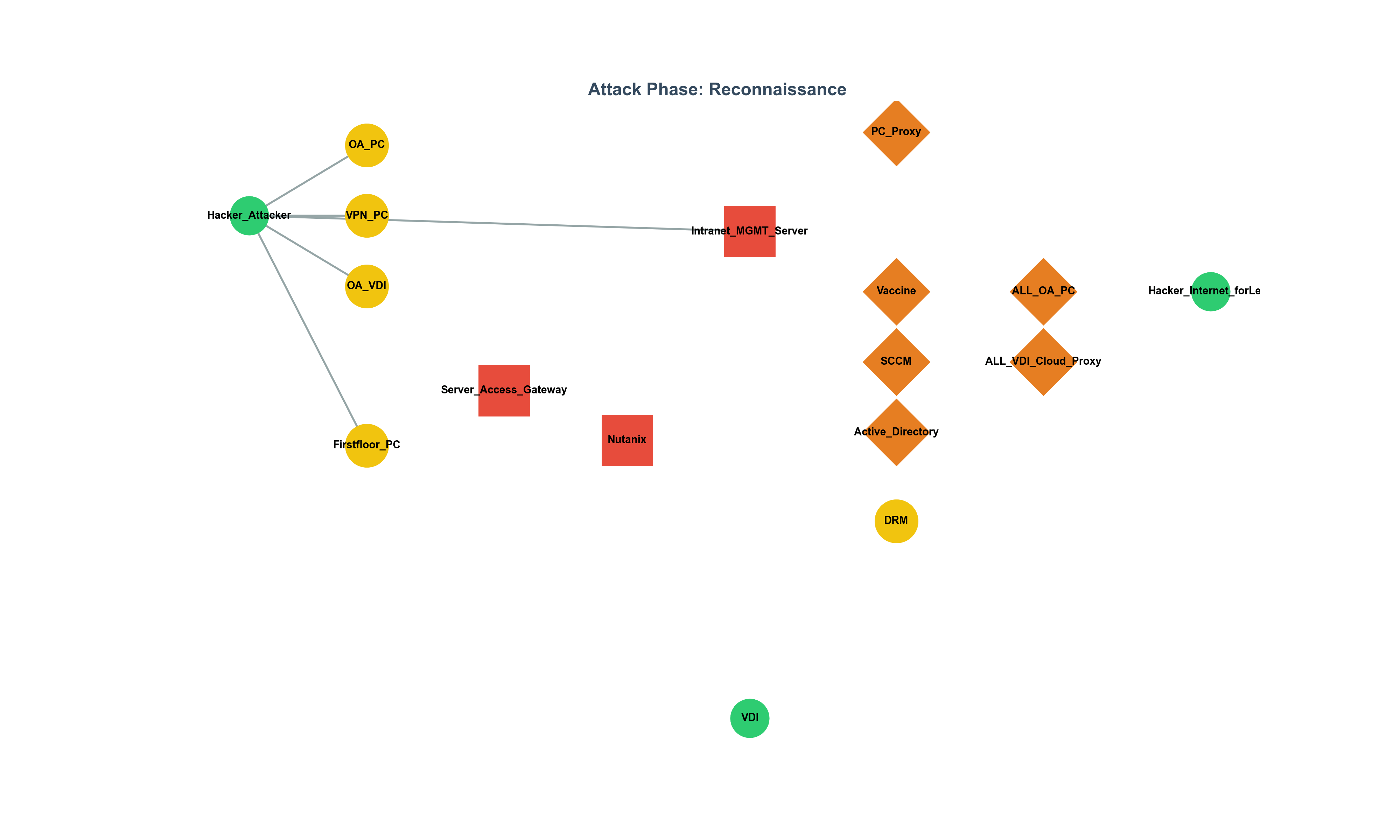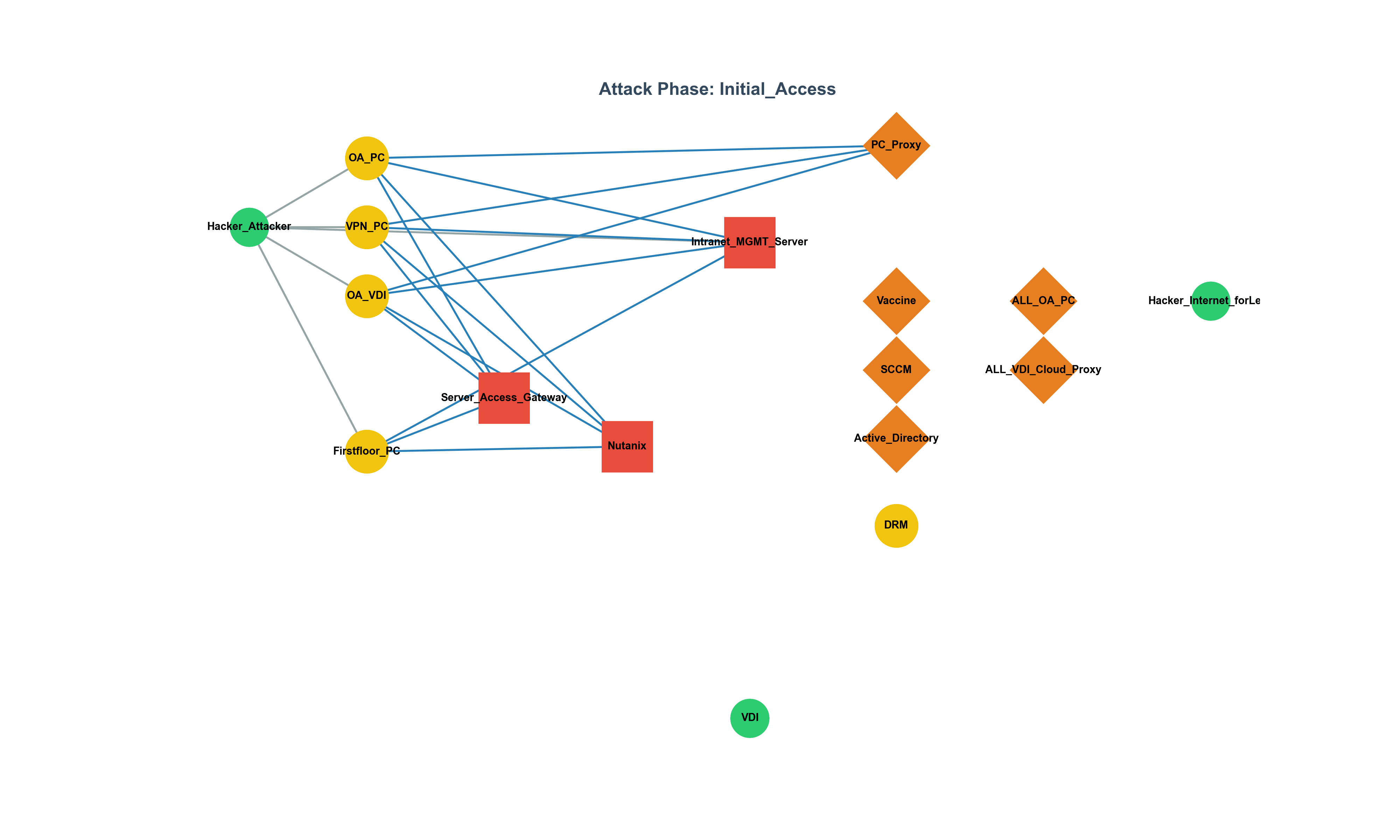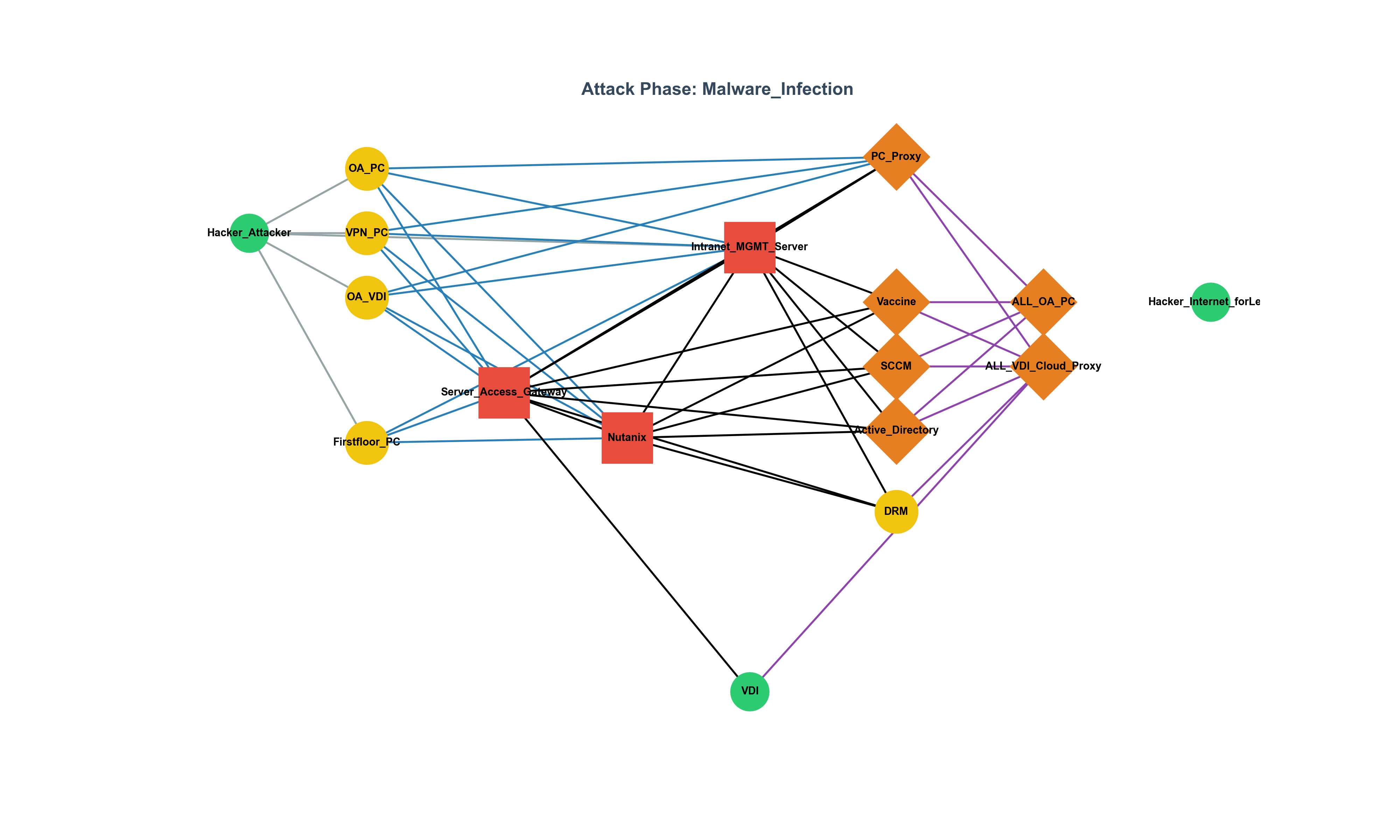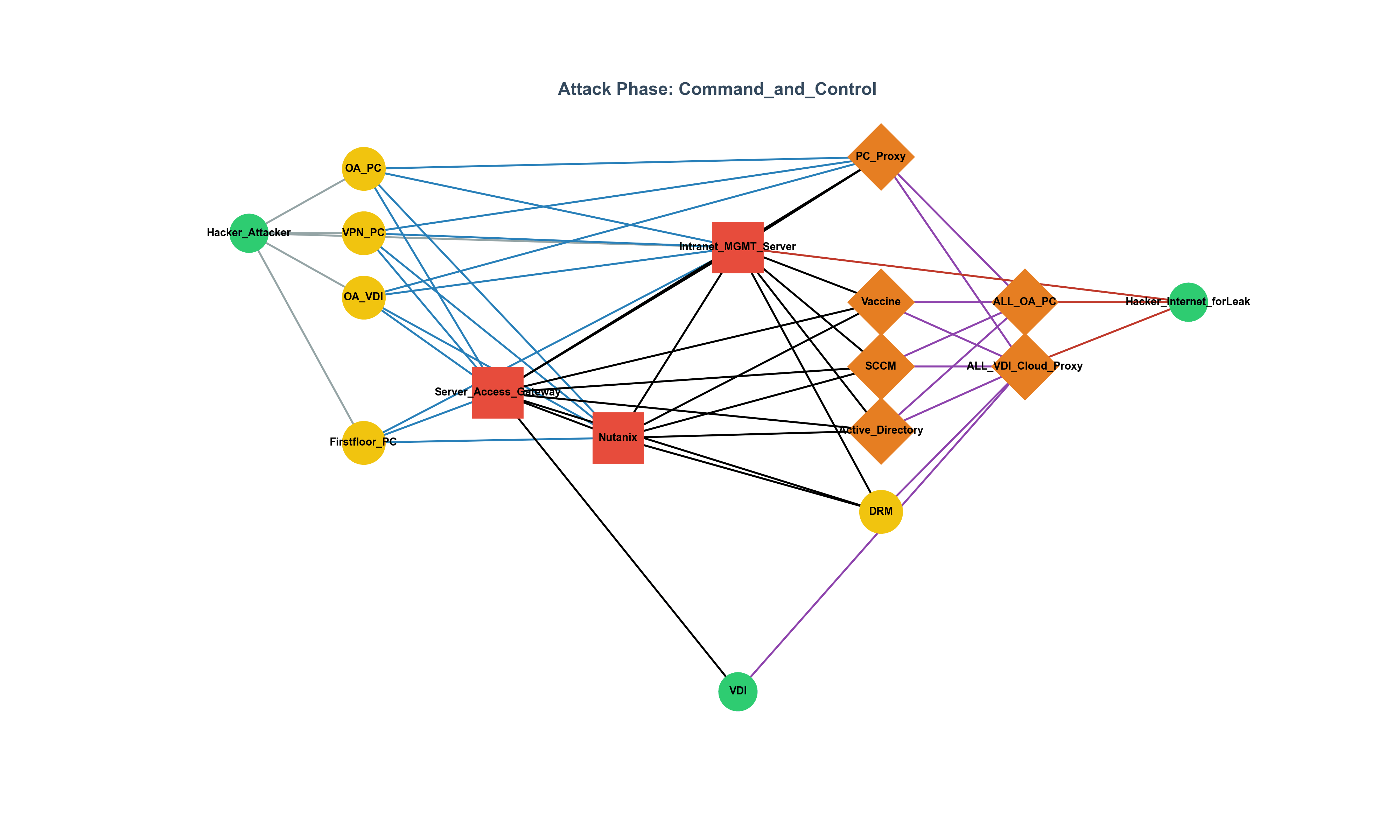
We live in an era overflowing with information and surging technology.
AI mimics human speech, summarizes thought, and even predicts intent.
But amidst all this, something vital is slowly being forgotten.
That is:
“Who thought of it first,”
“Who connected it,”
“Who gave it meaning.”
AI processes data. But insight belongs to humans.
To reinterpret the bypassing of Citrix VDI policies not as a mere technical vulnerability,
but as a legal violation,
a collapse of network isolation,
and a real-world regulatory failure—
that is not something AI can do.
It is a human act of context-building and
a creative synthesis of law, policy, and technical risk.
...