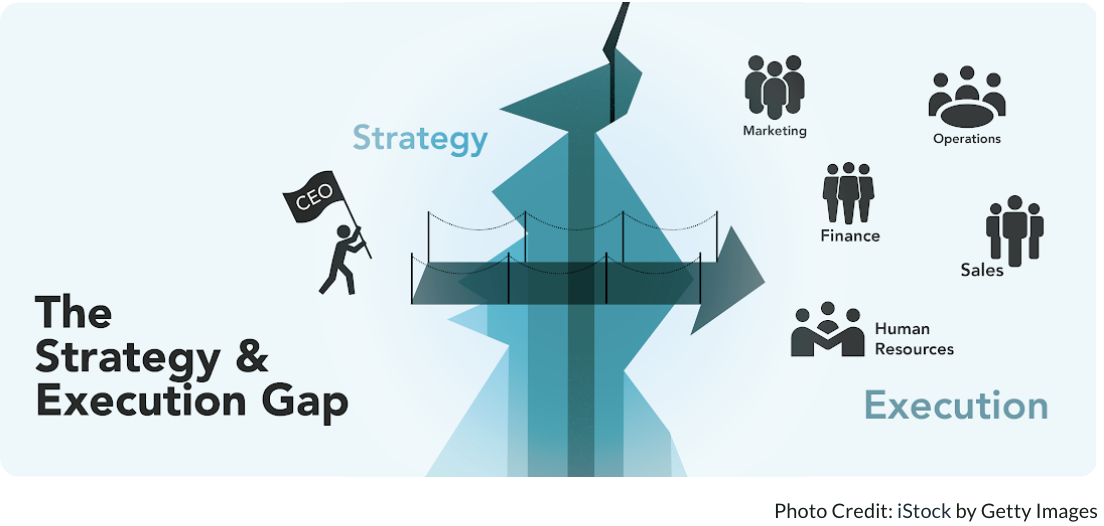
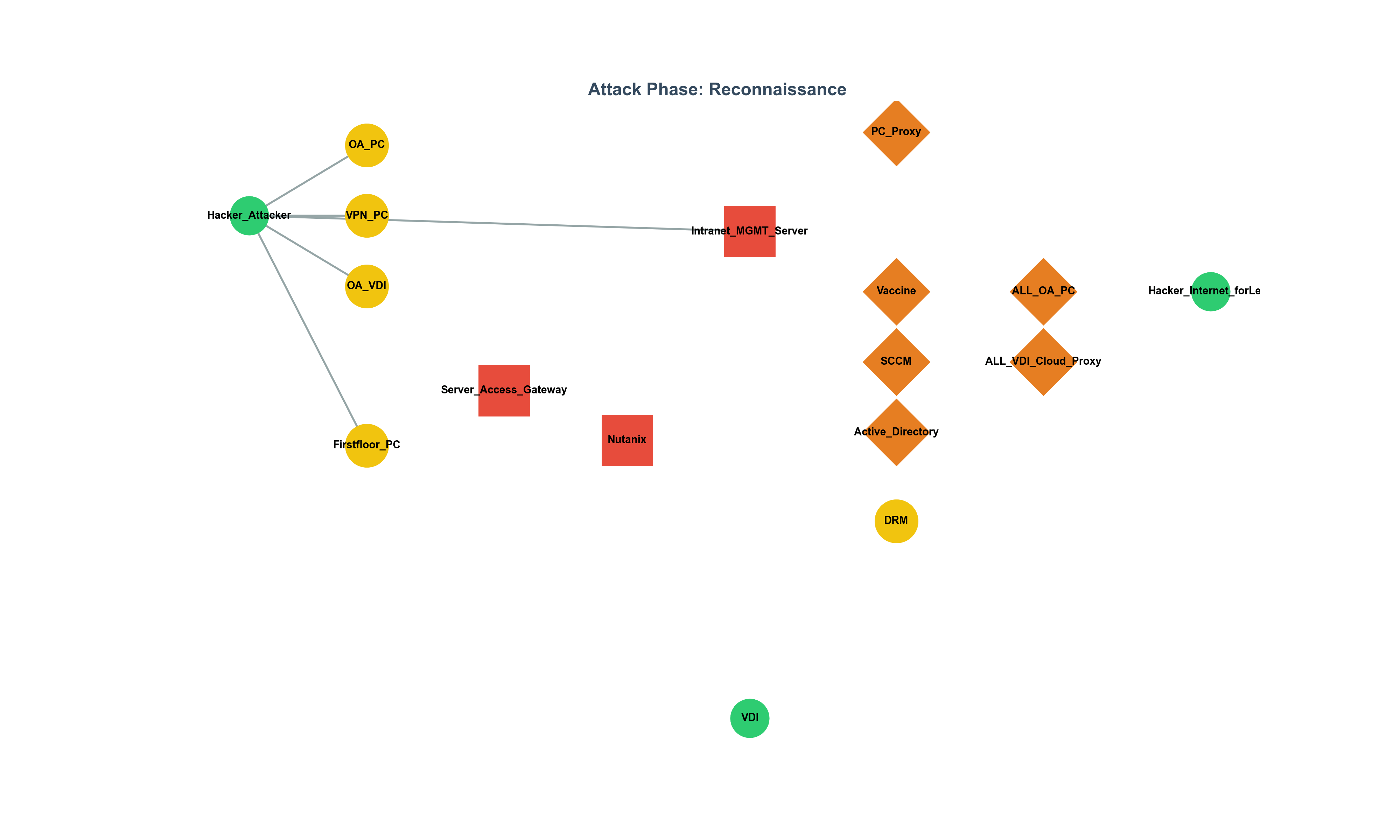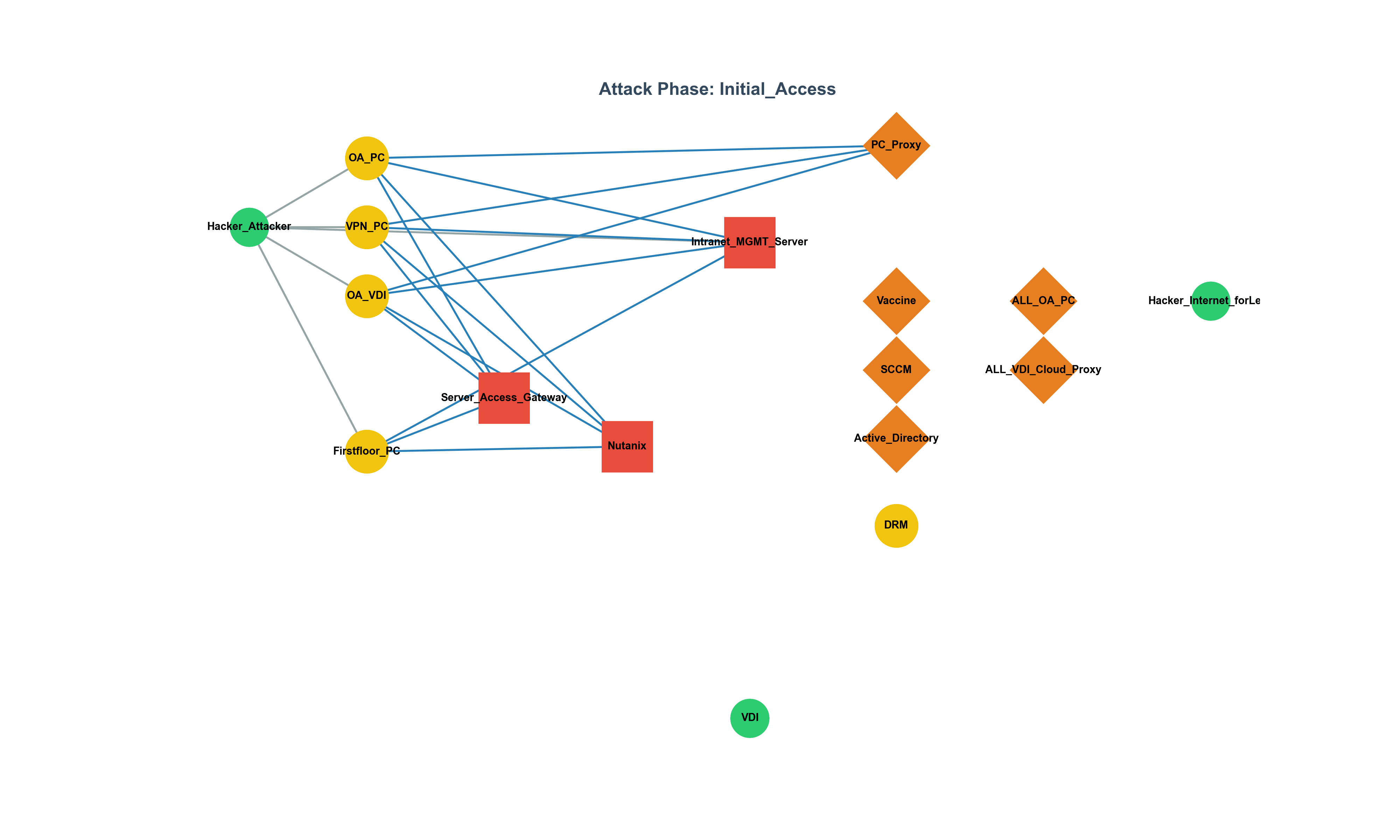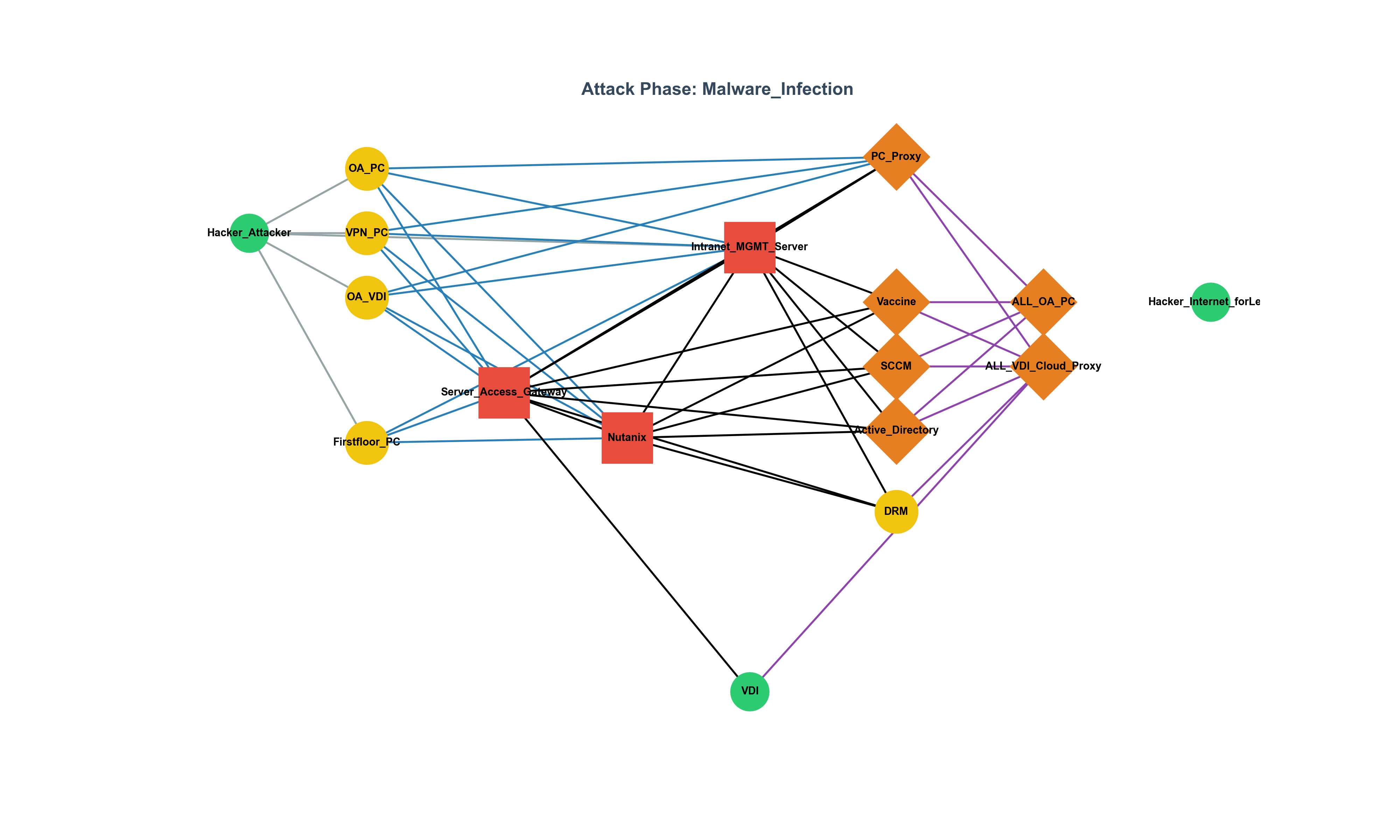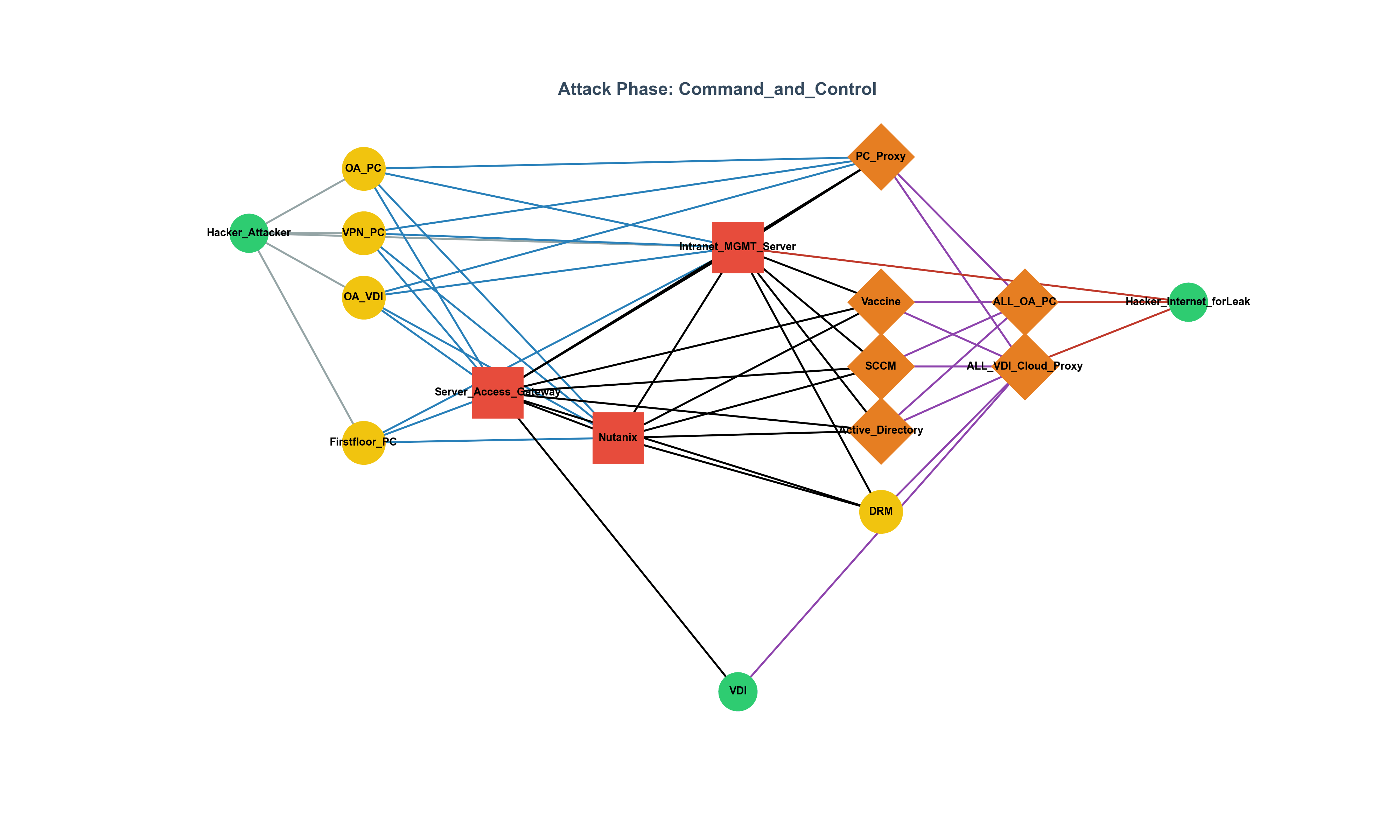
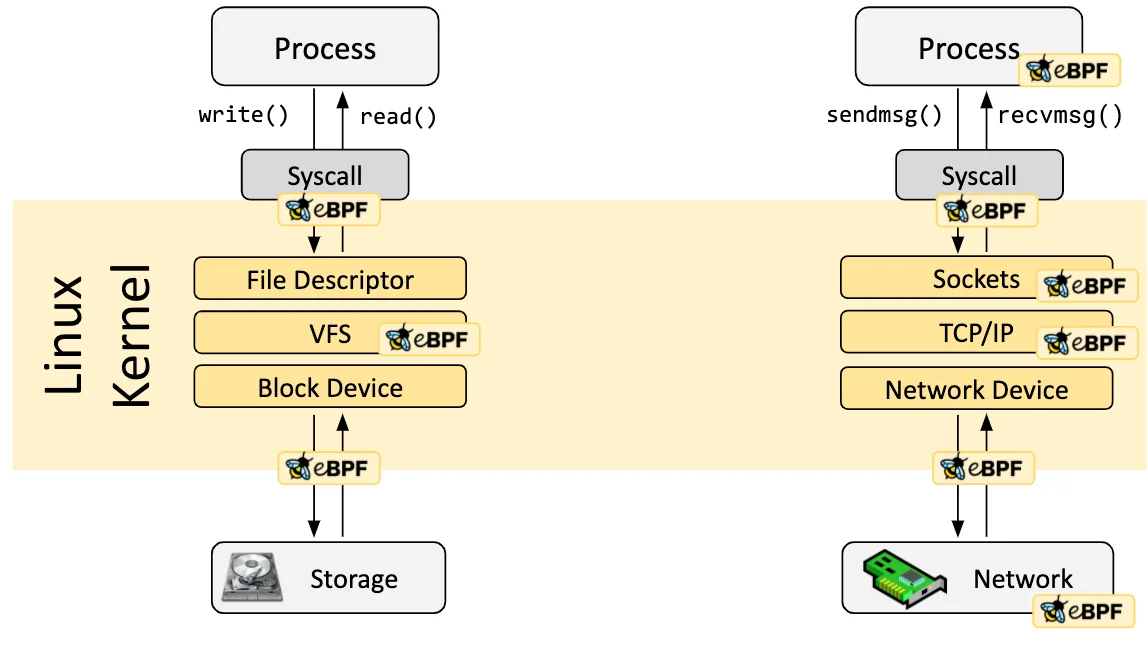
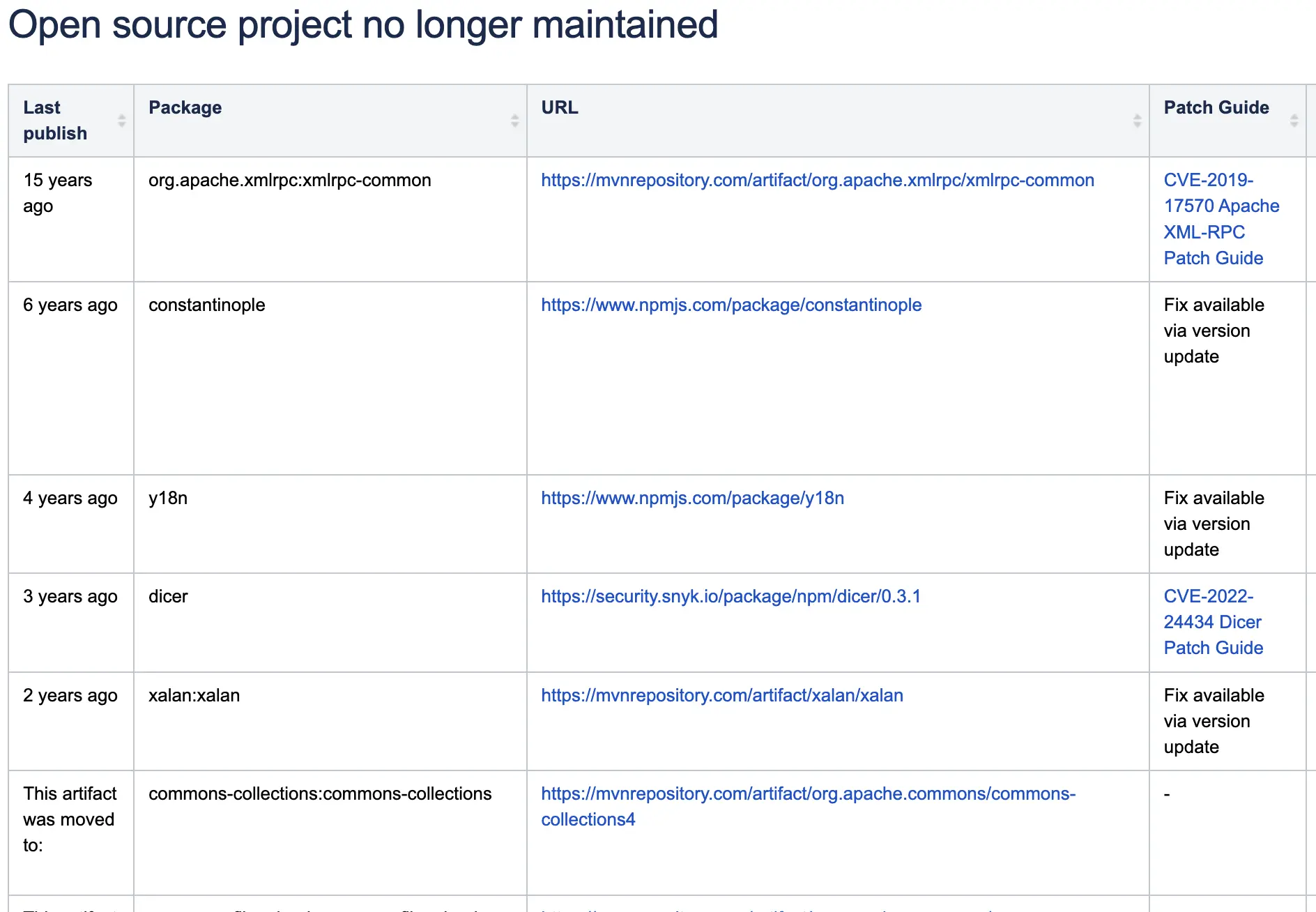
Can Development Culture Influence Security Levels? Evaluating Code Quality and Security Levels Using Static Analysis Tools (Joern) Background Unlike companies like Google with an open and collaborative development culture, in some organizations that lack such culture, the quality of the code, including security levels, can be heavily influenced by the individual’s capability. In particular, developers who tend to write poor quality code, such as using the strcpy function, can have their code quality and security levels assessed by utilizing static analysis tools (Joern, CodeQL, etc.) with custom rules. As a result, even in situations where the development culture is lacking, code quality and security levels can be improved, leading to the production of good-quality code.
...