A governance, privacy, and operations comparison between the EU’s eIDAS 2.0 (EUDI Wallet) and Korea’s mobile ID plus private identity verification (CI/DI) ecosystem.
🔥 A Mind That Dissects Systems
🔥 Trust and Culture Beyond Technology
🔥 Code That Fixes, Not Just Runs
Amadey Malware: A Comparative Study of Static Detection vs Memory-Based Detection
Using Amadey as a case study, this post compares static signature detection and memory-based detection through structure, evasion difficulty, and YARA usage.
The Visibility Principle: How Internal Vulnerability Visibility Shapes Remediation Behavior
A practical, research-informed look at why transparent internal vulnerability visibility can increase remediation participation and improve patch outcomes—through accountability, perceived surveillance, and deterrence mechanisms.
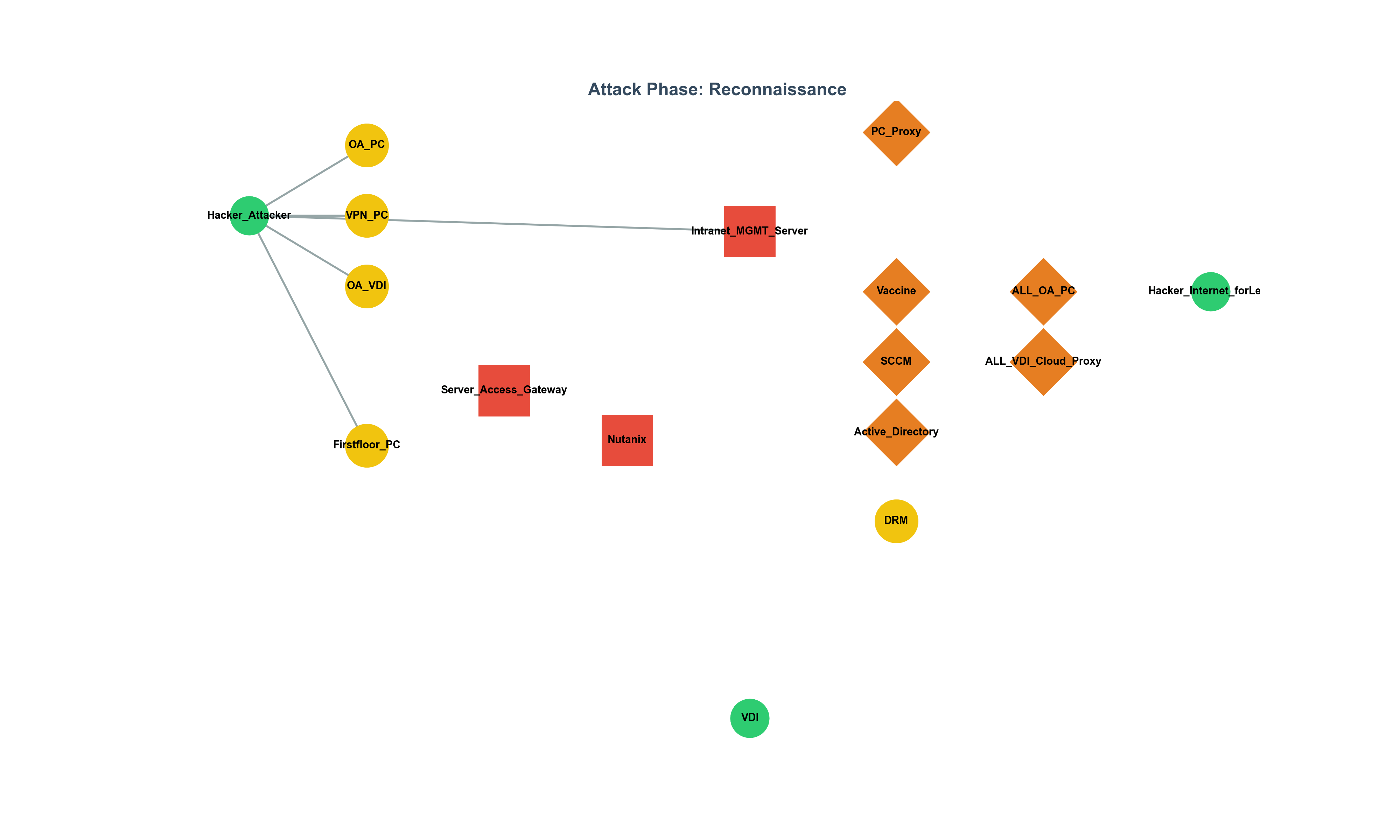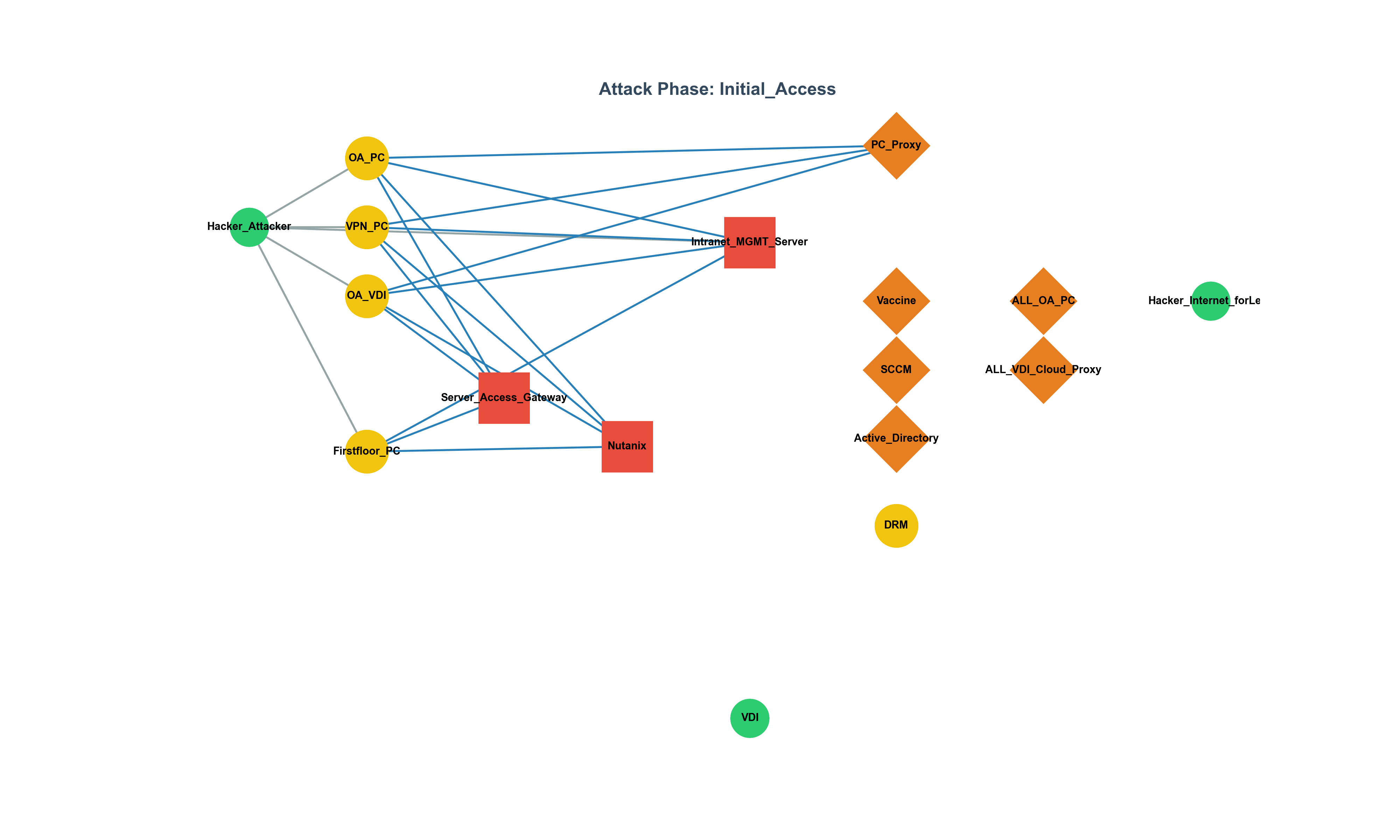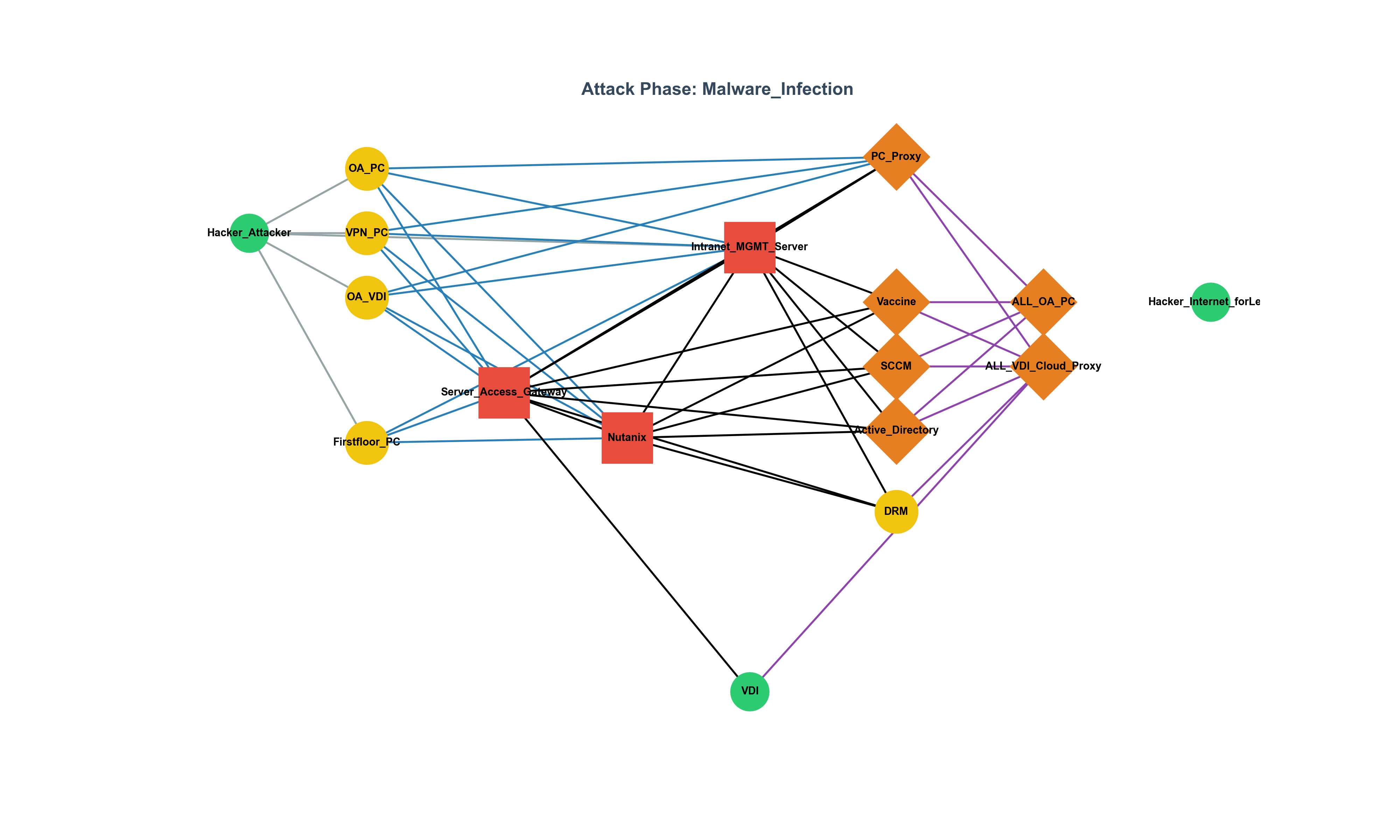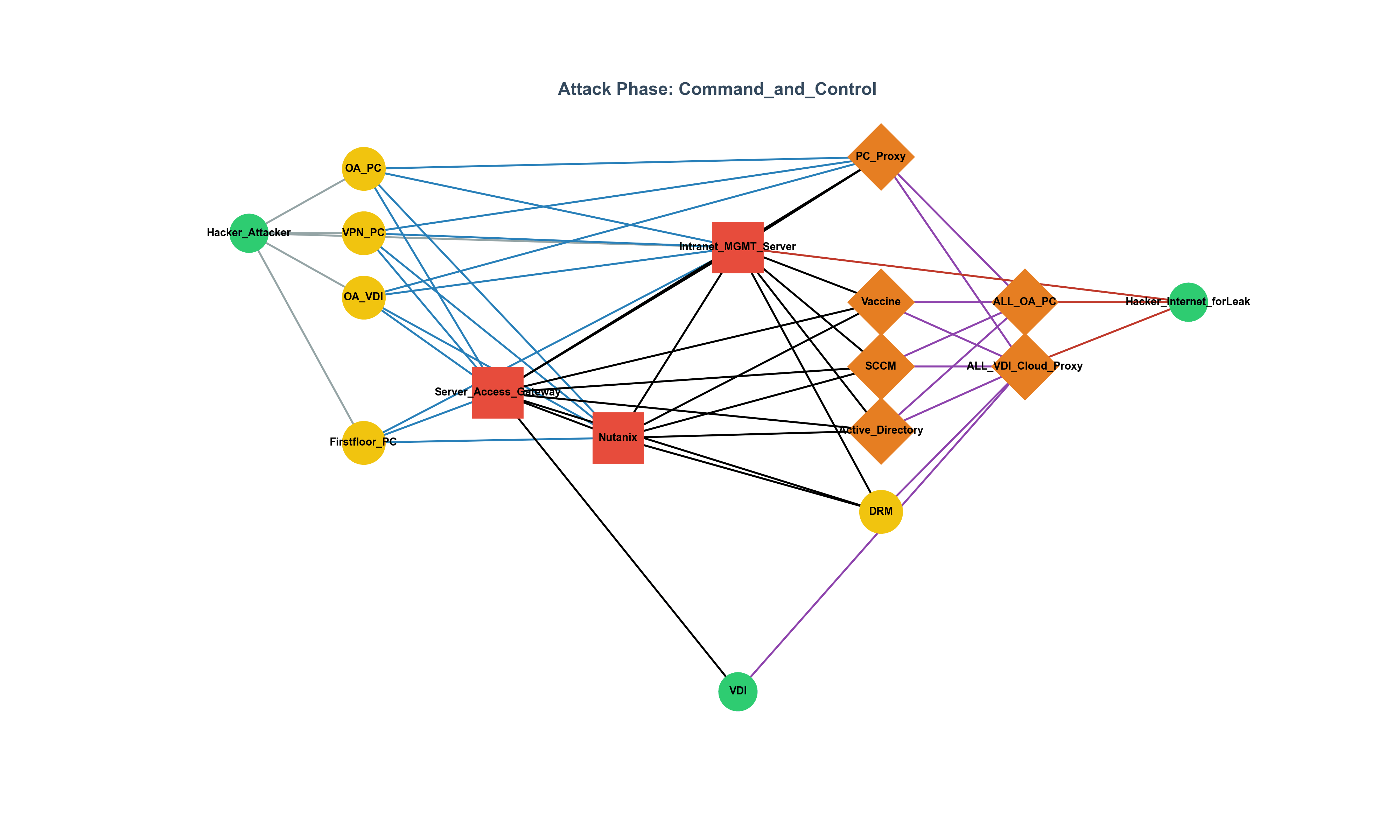
Attack Surface Management in 2025: Why Continuous Visibility is Essential
Why continuous visibility and attack surface management (ASM) are essential in 2025, with key trends, survey insights, and practical takeaways.
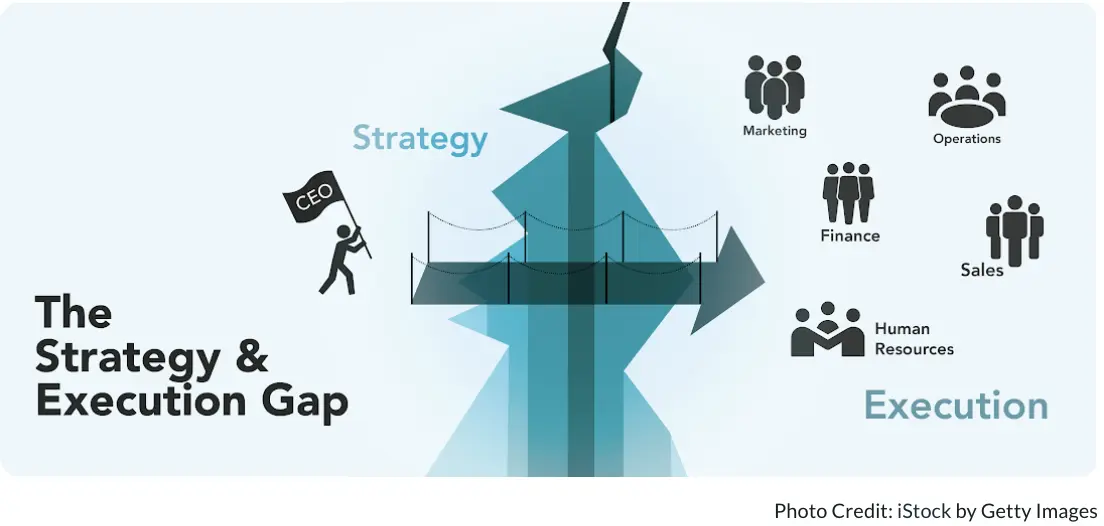
The Gap Between CISO Strategy and Execution: The WAF Debate and Field Leadership Report
Preface: The Crack Between Philosophy and Execution First half of 202x. When the group’s penetration test report stated, “SQL Injection possible in WAF-unprotected section,” the CISO was silent for a while. The report was blunt, the attack was classic, and there was no defense. “Was I wrong? Or did they misunderstand my intention…?” The CISO was a leader of strong conviction. He believed that with a strategy of “IPS + security by design,” it was possible to build a system robust enough to forgo WAF deployment. In fact, for years, this strategy contributed to the organization’s threat detection and incident prevention. ...
The Limitations of 'Secure' SSRF Patches: Advanced Bypasses and Defense-in-Depth
No Silver Bullet: Folklore & Modern Meaning The phrase “no silver bullet” originated in European folklore, where silver bullets were believed to be uniquely effective against supernatural creatures like werewolves or vampires. The earliest documented use appears in Walter Scott’s 1816 Tales of My Landlord, and historical cases such as the 1765 Beast of Gévaudan reference silver bullets as a last resort against mysterious threats. Over time, the expression evolved: today, “no silver bullet” means there is no single, simple solution to complex problems—a message popularized in software engineering by Fred Brooks’ 1986 essay. This post applies that lesson to SSRF defense: beware of one-size-fits-all fixes, and look deeper than folklore or quick patches. ...
Exception Serialization Patterns in OpenStack Nova: Theoretical RCE Risks and Lessons Learned
Analysis of potential Remote Code Execution vulnerability in OpenStack Nova’s exception serialization mechanism, including multiple PoC scenarios and defense recommendations.
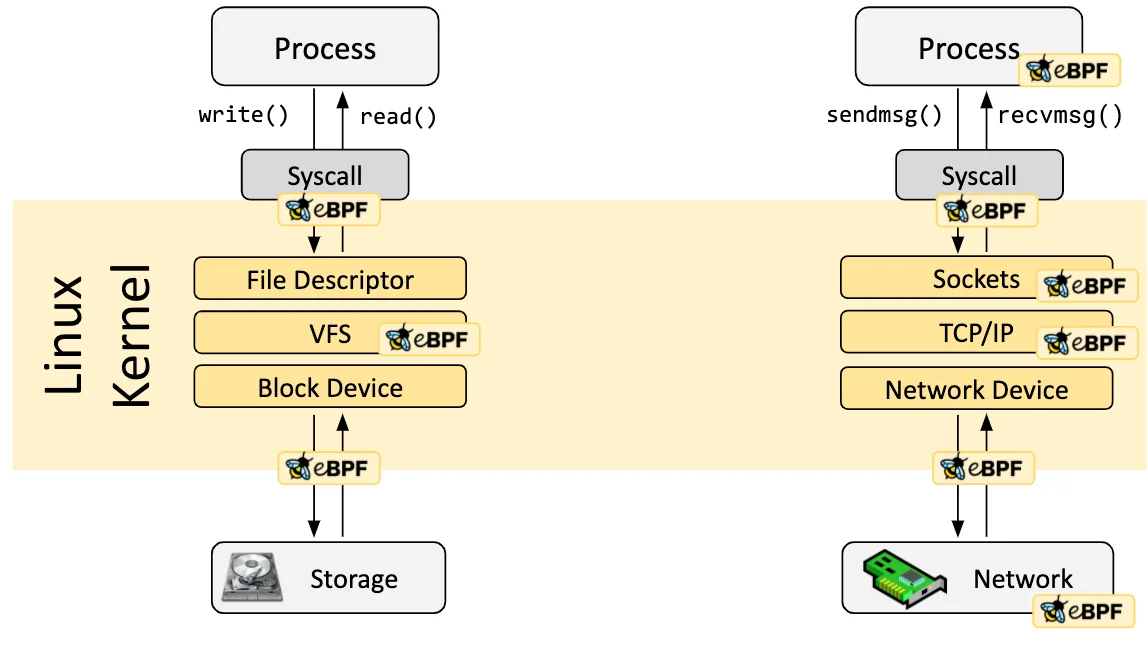
Endpoint Evasion Techniques (2020–2025): The Evolution of Attacks Bypassing EDR
This post analyzes the evolution of endpoint evasion techniques from 2020 to 2025. It covers BYOI, BYOVD, DLL hijacking, service tampering, and other sophisticated methods attackers use to bypass EDR and AV. Real-world ransomware cases and vendor impact are discussed, along with defensive insights.
SPOF in Cybersecurity: From History to Strategy, a Graph-Based Analysis
Analyzing the threat of Single Points of Failure (SPOF) through historical examples and graph theory, this piece presents a strategic approach to identifying and mitigating structural weaknesses in cybersecurity infrastructures.
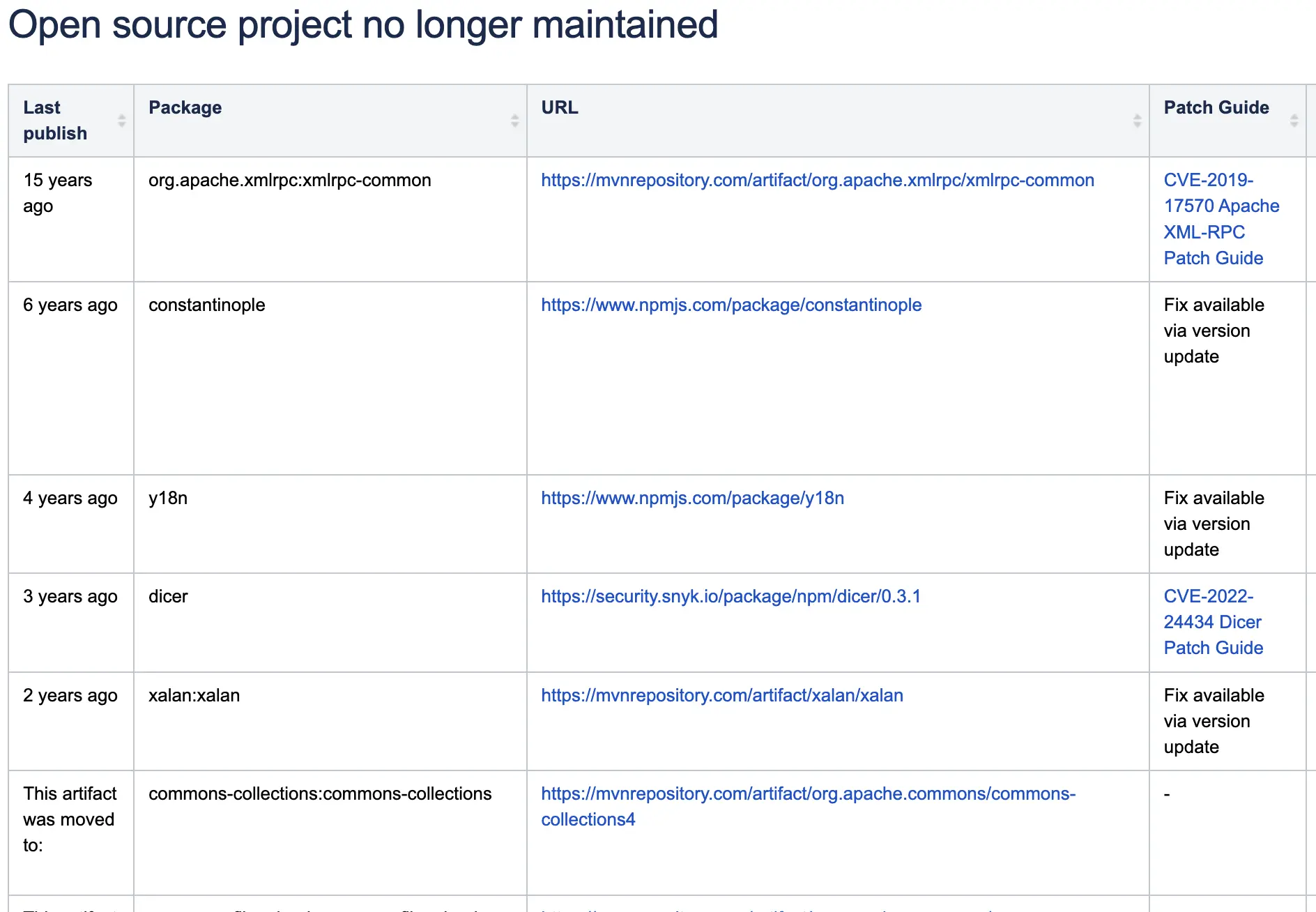
Dicer Module Vulnerability Mitigation Guide: CVE-2022-24434
This guide analyzes a vulnerability in the Dicer module indirectly affecting Multer, and provides a practical mitigation strategy. It serves as a real-world example of dealing with unmaintained open source dependencies.